4.9 Integration with MetaDefender Vault
About MetaDefender Vault
From MetaDefender Vault's documentation: "MetaDefender Vault (previously Metadefender Secure File Transfer) offers a safe process for transferring files to and from secure networks as well as a way to safely store and limit access to files. With the native integration between MetaDefender Vault and Metadefender Core, you can be sure that only files that were not detected as a threat will be accessible by your organization.
By integrating MetaDefender Vault with MetaDefender Email Gateway Security you will be able to investigate blocked files easier, store the original version of sanitized files on a separate storage, save email storage by replacing attachments with URLs and more.
Inline images
To maintain a good end user experience MetaDefender Email Gateway Security won't upload/delete inline images when integrated with MetaDefender Vault.
Example use cases
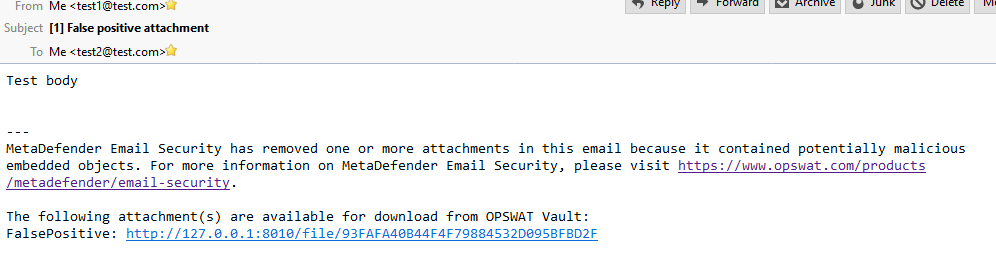
Accessing false positive attachments
Having an attachment removed because of a false positive scan result can harden both the end users and the administrator's everyday life. By enabling MetaDefender Email Gateway Security to upload blocked files to MetaDefender Vault an end-user can try to download the file from Vault later. MetaDefender Vault can rescan files periodically so if a file becomes clean later the user will be able to download it.
You can also give a protection about false negatives. For more information please check MetaDefender Vault's Outbreak Prevention.
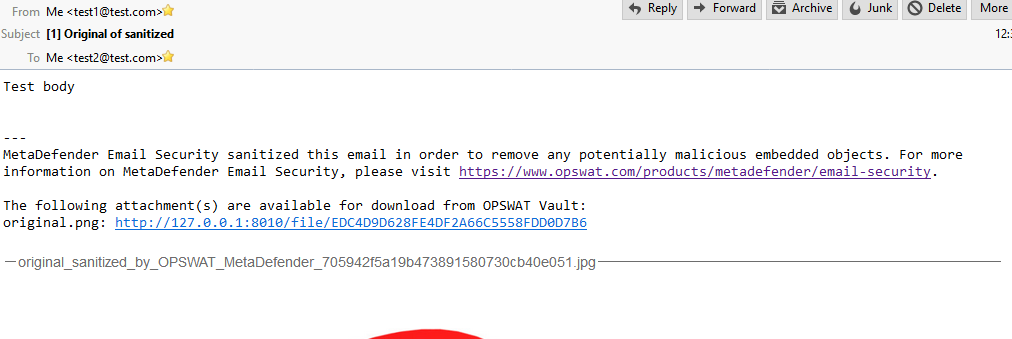
Accessing original version of sanitized files
If you have sanitization enabled for emails you may would like to access the original files or have them on a separate storage. You can configure MetaDefender Email Gateway Security to upload original versions of sanitized files and add URLs for accessing them into the modified email.
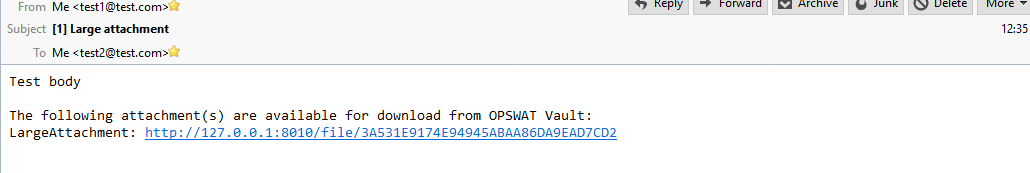
Sending larger attachments and saving email storage
MetaDefender Email Gateway Security can upload your attachments to MetaDefender Vault while removing them from the original email and adding URLs for accessing them. This feature makes possible for end users to send/receive attachments which exceeds the email server's file limit and it can also save precious storage space on your email server.
Prerequisites and limitations
You will need a running and accessible MetaDefender Vault and an API token which can be used for uploading files. Please check this page for more information about API tokens. Authentication requirement for downloading files should be turned off on MetaDefender Vault.
No MetaDefender Vault related action will take place for emails with blocked content if the selected action in the security rule is to block the whole email.
Configuring Security Rules
You can setup MetaDefender Vault for every security rule separately under the "Vault" tab. If you want to upload attachments in a given security rule you should enable "UPLOAD ATTACHMENTS TO VAULT" and configure the following settings.
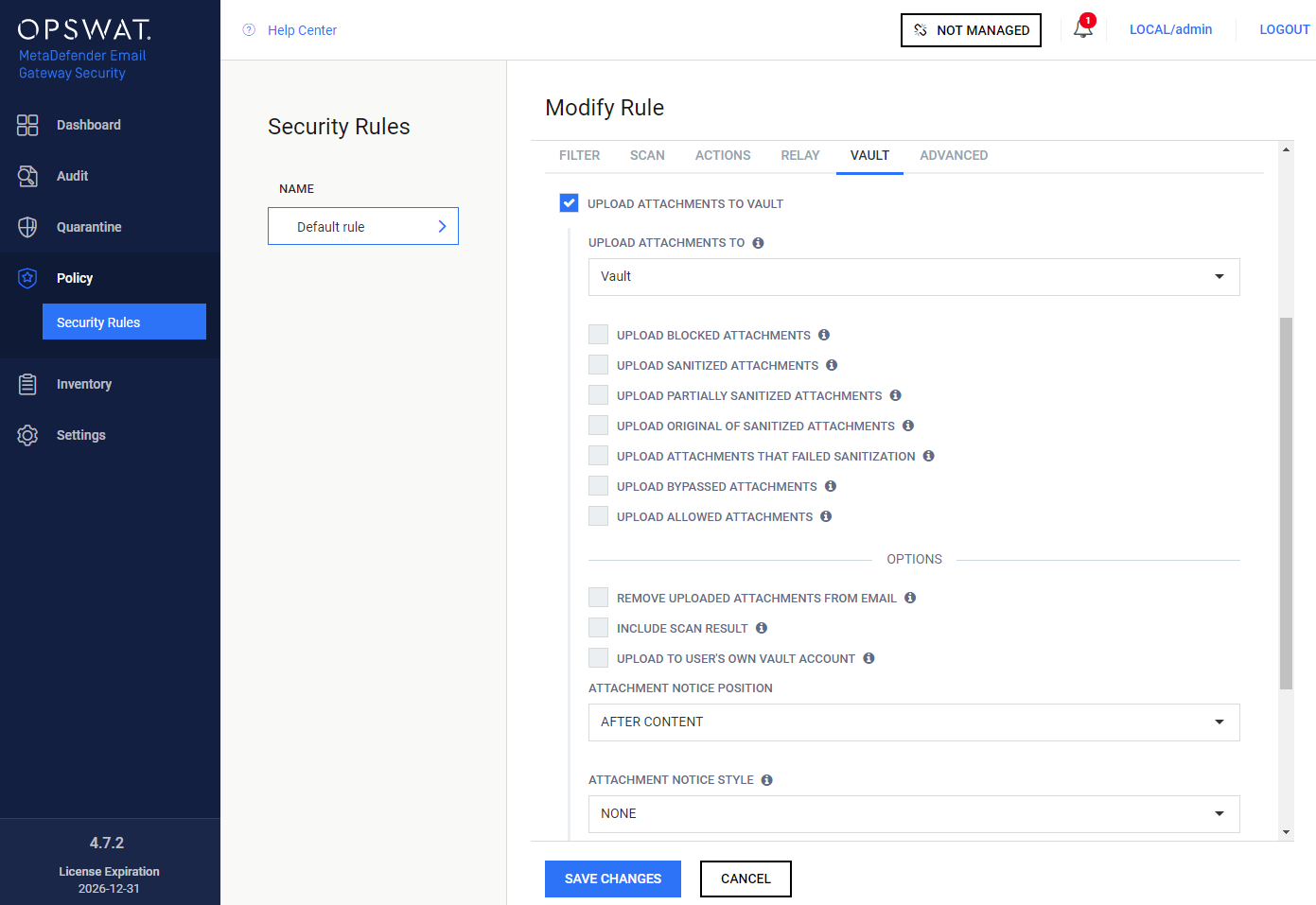
Upload attachments to
The MetaDefender Vault type server profile must be specified here to which the attachments will be uploaded according to the configuration below.
Uploaded attachment types
You can select which attachments to upload based on their scan verdicts.
Upload blocked attachments
By selecting this option every attachment which was blocked will be uploaded to MetaDefender Vault.
Upload sanitized attachments
By selecting this option every attachment which was sanitized will be uploaded to MetaDefender Vault.
Upload partially sanitized attachments
By selecting this option every attachment which was partially sanitized will be uploaded to MetaDefender Vault.
This requires the 'Distinguish partial archive sanitization result' option checked in the MetaDefender Core rule used to scan content with. See MetaDefender Core > 3.6.2. Workflow template configuration for more information.
Upload original of sanitized attachments
By selecting this option every attachment which was an origin for a sanitized one will be uploaded to MetaDefender Vault.
Upload attachments that failed sanitization
By selecting this option every attachment where the sanitization failed will be uploaded to MetaDefender Vault.
If both
-
UPLOAD ORIGINAL OF SANITIZED ATTACHMENTS and
-
UPLOAD ATTACHMENTS THAT FAILED SANITIZATION
are enabled –and the sanitization fails– then the original file will be uploaded only once.
Upload bypassed attachments
By selecting this option every attachment that was bypassed by Email Gateway Security will be uploaded to MetaDefender Vault.
Upload allowed attachments
By selecting this option every attachment which was allowed will be uploaded to MetaDefender Vault.
Allowed vs original of sanitized
Please note that if an attachment is allowed but gets sanitized then it won't be uploaded if only the "Upload allowed attachments" is selected. If you want to upload these kind of attachments you should have "Upload original of sanitized attachments" enabled.
Options
Remove uploaded attachments from email
By enabling this option every attachment which was successfully uploaded to MetaDefender Vault will be removed from the email. If uploading an attachment fails the removal will be skipped. Blocked files will be removed regardless this setting if the action for blocked contents is to "Delete blocked contents".
Include scan result
By enabling this option, Email Gateway Security will upload the scan results to Vault besides the attachment as metadata. As a result Vault will know the verdict of the scan and can make the file available immediately.
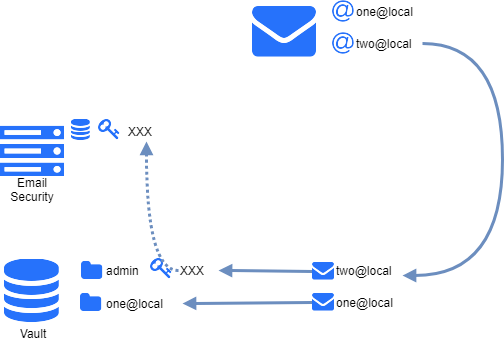
Upload to user's own vault account
Depending whether the email was matched by an inbound or an outbound rule, based on the email addresses, the files will be uploaded to the recipients' (inbound) or senders' (outbound) own Vault accounts (when the account exists on the Vault at all). This feature requires appropriate permissions (impersonation) on Vault.
If no account exist with the recipient email address on the Vault, then the file will be uploaded to the account that is assigned to the API key specified in the MetaDefender Vault type server profile set for the matching rule.
Example
Attachment notification
You can setup custom notification text for plain text and HTML emails and you can also select the position of the notification (before or after the original content).
Removal of URL list placeholder
You should not remove %[]vault_list[]% from the notification texts as it would lead to missing URLs.
Browsing email attachments in MetaDefender Vault
MetaDefender Email Gateway Security will upload attachments to MetaDefender Vault using this folder structure for easier browsing: "MetaDefender Email Gateway Security/<date>/<subject>_<<sender address>>_<<message id>>/".
For example:
-
MetaDefender Email Gateway Security
-
2018-09-28
-
Test subject_<test1@local>_<12345>
-
Attachment 1
-
Attachment 2
-
-
Test subject 2_<test1@local>_<No Message Id (456)>
-
Attachment 1
-
-
-
2018-09-27
-
Test_<test1@local>_<555>
-
Attachment 1
-
-
-
No message ID
If an email doesn't have a message id "No Message Id (<random ID>)" will be used instead for unique identification.
Lookin up emails on Vault
Knowing an email's message ID or sender address (you can easily check it in email details) makes it simple to look the email up using the Vault's search functionality.
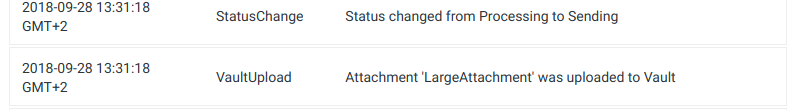
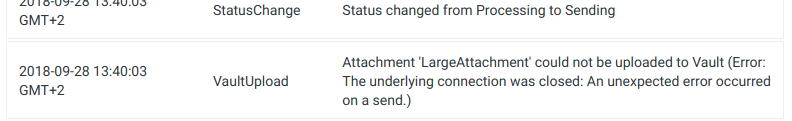
Upload information in Processing history
You can find information about attachment upload to Vault in the processing history of an email. You will see if an attachment was successfully uploaded or if there was some error while uploading it.
Successful upload:
Failed upload:
Troubleshooting
Problems during upload
If you are getting errors for upload please check the followings:
-
Vault URL is correct:
-
You are using the correct format: http(s)://<host>:<port>/vault_rest
-
You are using http scheme for Vault without HTTPS and using http scheme for Vault with HTTPS
-
You are using the port for REST API and not the port for UI
-
-
Vault API key is correct
-
Vault is accessible from the machine where MetaDefender Email Gateway Security is installed
-
If Vault is used with HTTPS enabled then the certificate can be trusted on the machine where MetaDefender Email Gateway Security is installed
Unexpected host in MetaDefender Vault URLs
URLs inserted into emails are generated by MetaDefender Vault. If you experience URLs with unexpected host in them then you should configure MetaDefender Vault's host which is used for accessing the UI and link generation. More information can be found here.