3.4 General settings
Global settings

Notification and report settings
The following properties can be set:
-
SMTP SERVER: defines what SMTP servers MetaDefender Email Gateway Security should use to send notification and report emails.
This value is an SMTP type server profile. For details about server profiles see 3.7 Server profiles.
The following functions, notifications and reports use this setting:-
Quarantine reports (4.3 Quarantine)
-
Quarantine forward (4.3 Quarantine)
-
Quarantine release (4.3 Quarantine)
-
Notification emails
-
-
PUBLIC SERVER ADDRESS: this is the IP or DNS address that will be used in notifications and reports to identify this server. When left empty there won't be any links in the notification and reports to this instance.
When setting this property please be aware that this address may be sent for recipients outside of your company (e.g. in a notification about password protected document).
-
RESCAN LINK AVAILABILITY: the time window (in hours) while the link is allowed to be used to initiate rescanning an email.
-
USE THE SERVER'S LOCAL TIMEZONE INSTEAD OF UTC: instead of using UTC in dates in notifications/disclaimers MetaDefender Email Gateway Security will use the server's timezone where it is installed
Inbound SMTP settings
In this sections properties of MetaDefender Email Gateway Security's SMTP service can be set. MetaDefender Email Gateway Security receives emails on this interface from any kind of its mail sources (email gateway, mail server, etc., see 1.6 Email traffic redirection).
The following properties can be set:
-
SMTP PORT: TCP port of the SMTP service
-
ENCRYPTION
-
None: no encryption is used for communication with SMTP service,
-
StartTLS optional: StartTLS may be used if the client chooses to use it,
-
StartTLS required: using StartTLS is mandatory.
StartTLS optional and StartTLS required are applicable only if TLS is configured.
For details see 3.2 Configuring TLS.
-
Sender Policy Framework lookup
Sender Policy Framework ( SPF ) is a mechanism defined by RFC 7208 which can help determine if incoming mails are sent from a host authorized by the domain's administrators. Usually a domain administrator will publish a TXT record in the Domain Name System (DNS) in order to specify a list of authorized hosts that can send emails from that domain. Enabling SPF is an anti-spam technique that will instruct MetaDefender Email Gateway Security to perform SPF checks on the "FROM" address(es) and add a header to the email with the SPF result.
For further details see Sender Policy Framework (SPF) for Authorizing Use of Domains in Email.
The following option is available:
-
PERFORM SPF LOOKUP ON EXTERNAL IP ADDRESSES: perform the SPF lookup on external IP addresses from which emails were submitted
SPF results
After the SPF check is performed the X-Metadefender-Spf-Result header will be added to the email and the value will be one of the following:
|
Header value |
Description |
|
Pass |
A pass result is an explicit statement that the client is authorized to inject mail with the given identity. |
|
NoRecord |
A result of norecord means either
|
|
SoftFail |
A softfail result is a weak statement by the publishing ADMD that the host is probably not authorized. It has not published a stronger, more definitive policy that results in a hardfail. |
|
HardFail |
A hardfail result is an explicit statement that the client is not authorized to use the domain in the given identity. |
|
Error |
An error result means the SPF verifier encountered a transient (generally DNS) error while performing the check. A later retry may succeed without further DNS operator action. |
|
Neutral |
A neutral result means the ADMD has explicitly stated that it is not asserting whether the IP address is authorized. |
|
Unknown |
An unknown result means the domain's published records could not be correctly interpreted. This signals an error condition that definitely requires DNS operator intervention to be resolved. |
|
UnknownMechanism |
An unknownmechanism result means that the ADMD uses a mechanism not recognized by this client. |
DKIM signature verification
DomainKeys Identified Mail ( DKIM ) is a mechanism defined by RFC6376. It is an email authentication method designed to detect forged sender addresses in emails ( email spoofing ), a technique often used in phishing and email spam .
The following option is available:
-
VERIFY DKIM SIGNATURES verify DKIM signatures for processed emails
DKIM results
After the DKIM check is performed the X-Metadefender-Dkim-Result header will be added to the email and the value will be one of the following:
|
Header value |
Description |
|
Valid |
Signature verification was successful and email has not been modified since submission. |
|
Invalid |
Signature verification was NOT successful and this email could be forged/modified during its transit. |
|
Empty |
No DKIM signature header was found in the email. |
|
Error |
An unexpected error occurred while attempting to verify the DKIM signature. |
Retry settings
If MetaDefender Email Gateway Security fails to connect the Core or the relay SMTP servers during the processing of an email, then the connection attempt will be retried according to the settings below.
Retry settings under Settings > Global settings apply to reconnection attempts to both Core and the configured SMTP servers.
If the connection succeeds to the Core after a certain number of attempts (but before it is exhausted), then the RETRY COUNT counter is reset for the retry attempts connecting to the SMTP servers.
The following properties can be set:
-
RETRY COUNT: how many times to try to resend the email –in case of failure– to all the relays (see 4.2 Security rules) before giving up
-
RETRY INTERVAL: base factor (in seconds) to wait before next resend attempt
Deployment mode
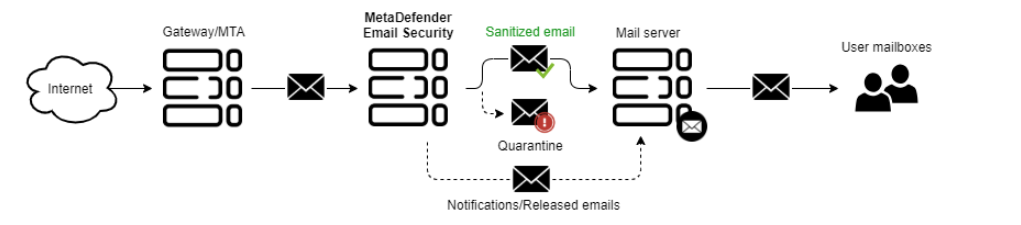
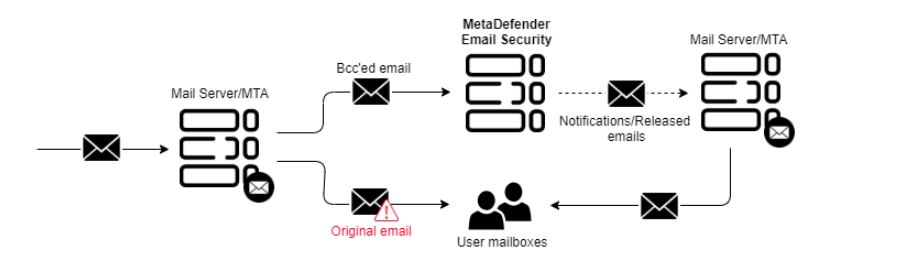
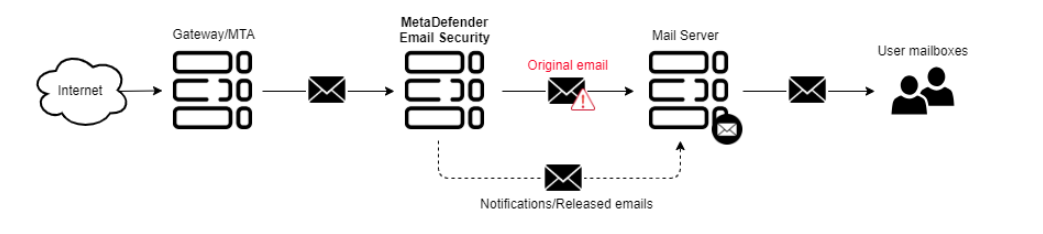
Deployment mode options are used to evaluate/test MetaDefender Email Gateway Security without necessarily affecting your existing email traffic. The following deployment modes are available:
|
|
Diagram |
Notes |
|
PROTECTION MODE |
|
Use this mode when you deploy MetaDefender Email Gateway Security in a production environment. This mode will protect your emails from malicious and untrusted content. |
|
OUT-OF-BAND MONITORING MODE |
|
Use this mode ONLY when you want to evaluate MetaDefender Email Gateway Security in an out-of-band scenario. This mode will NOT deliver any processed email. It requires you to send copies of emails to MetaDefender Email Gateway Security for processing. |
|
INLINE MONITORING MODE |
|
Use this mode ONLY when you want to evaluate MetaDefender Email Gateway Security without making modifications to processed emails. This mode will NOT protect your emails from malicious or untrusted content. |
Data retention
Data retention settings may be configured under Settings > Data retention.
The following properties are available for configuration:
-
Email history clean up: audit records under Dashboard > Email history will be retained for the time configured here.
-
OFF: Switch off automatic clean up.
-
1 HOUR .. 12 MONTHS: history records are automatically deleted after reaching the age specified by the configuration value.
Only records with permanent, non-failure statuses (Completed and Deleted) are cleaned-up.
-
-
Refused email history clean up: history records under Dashboard > Refused emails will be retained for the time configured here.
-
OFF: Switch off automatic clean up.
-
1 HOUR .. 12 MONTHS: records are automatically deleted after reaching the age specified by the configuration value.
-
-
Quarantine clean up: quarantine items under Dashboard > Quarantine will be retained for the time configured here (except pinned items which are not affected by the automatic clean up).
-
OFF: Switch off automatic clean up.
-
1 HOUR .. 12 MONTHS: items are automatically deleted after reaching the age specified by the configuration value.
-
-
Audit records clean up: audit records under Dashboard > Config history will be retained for the time configured here.
-
OFF: Switch off automatic clean up.
-
1 HOUR .. 12 MONTHS: audit records are automatically deleted after reaching the age specified by the configuration value.
-