6.2.10 Version 4.7.1
4.7.1 MetaDefender Email Security releaseJuly 1, 2019 |
MetaDefender Email Security 4.7.1 is a maintenance release focusing on fixing a recent Central Management integration issue and on adding some minor improvements. |
||||
New & Improved |
|||||
SMTP server component of Email Security now listens on IPv6 when it is available |
MetaDefender Email Security's SMTP server component now listens on both IPv4 and IPv6 (if IPv6 is configured). |
||||
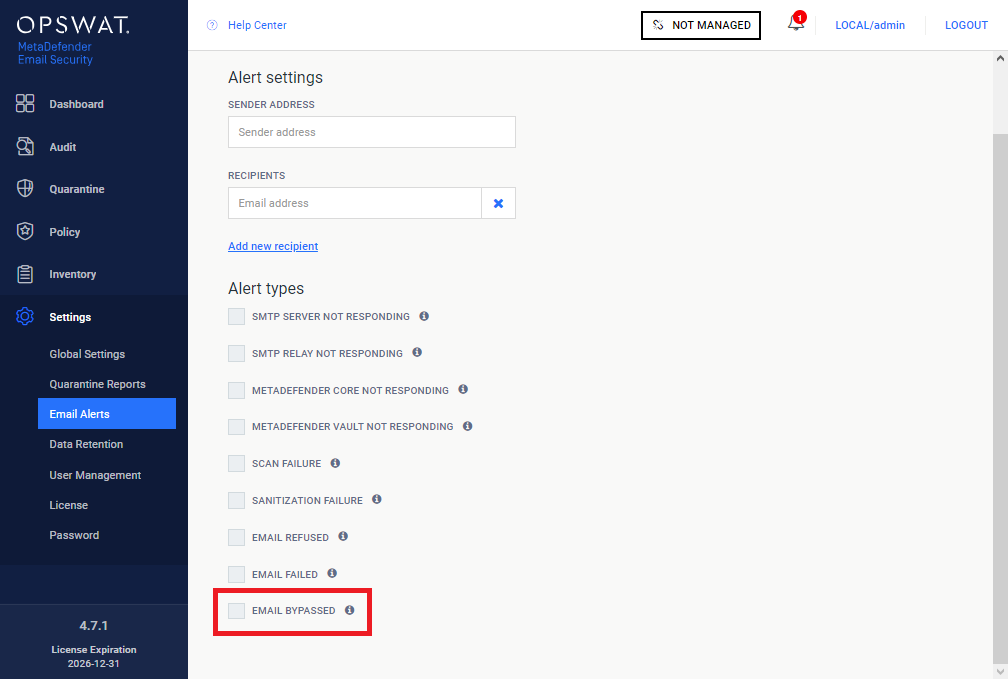
Email Security now has an option to send alert emails when emails get bypassed |
A new option is available under Settings > Email Alerts / EMAIL BYPASSED. If this option is enabled, then a notification will be sent if MetaDefender Email Security bypassed scanning an email. This alert will be sent for every bypassed email occurrence.
For details see the Email alerts section in 3.5.1 Configuration. |
||||
Emails get bypassed when there is no license (to ensure email business continuity) |
If MetaDefender Email Security's license is invalid, then it will bypass all emails. A bypass workflow is applied in these cases, meaning that the bypass disclaimer is applied to the email (if enabled at the matching rule) and a bypass alert email is sent (if enabled under Settings > Email Alerts / EMAIL BYPASSED ). For details about actions to bypass emails and bypass disclaimers see the Advanced scan settings section in 4.2 Security rules. For details about email alerts see the Email alerts section in 3.5.1 Configuration. |
||||
The default disclaimer for messages with encrypted contents have been updated |
The disclaimer message for password protected emails have been updated to help users to better understand the situation and the next steps.
For details about support for emails with password protected attachments see 4.7 Support for password protected attachments. For details about actions to handle emails with password protected attachments see 4.2 Security rules. For details about disclaimer variables see 4.2.1 Disclaimer variables. |
||||
Fixed |
|||||
Product schema is invalid error when adding Email Security to Central Management |
When trying to add MetaDefender Email Security 4.7.0 to the recent versions of Central Management, the operation fails and the Product schema is invalid error message is shown. This error is the result of some modifications introduced in Email Security 4.7.0, and that is fixed now. |
||||
Rescan pages of password protected attachments sometimes took very long to load |
MetaDefender Email Security can be configured to let users to provide the password for encrypted attachments and send the email with the decrypted contents to re-scan. Re-scanning can be initiated on a public page of Email Security. This page took in certain cases even minutes to load. For details about support for emails with password protected attachments see 4.7 Support for password protected attachments. |
||||
Certain emails got refused by the SMTP component without an apparent reason |
Email Security refused some emails on its SMTP interface without an apparent reason. These emails had contents with non-standard formatting. Email Security parser is now enhanced to be able to process even this kind of non standard compliant email formats. |
||||