4.2 Security rules
Security rules in MetaDefender Email Gateway Security can be configured under Policy > Security rules.
In traditional configurations MetaDefender Email Gateway Security is wedged between the organization's email gateway and mail server (see the image below). In case of inbound email directions it receives the email from the email gateway and sends it towards the mail server. In case of outbound directions it receives the email from the mail server and sends it towards the email gateway.
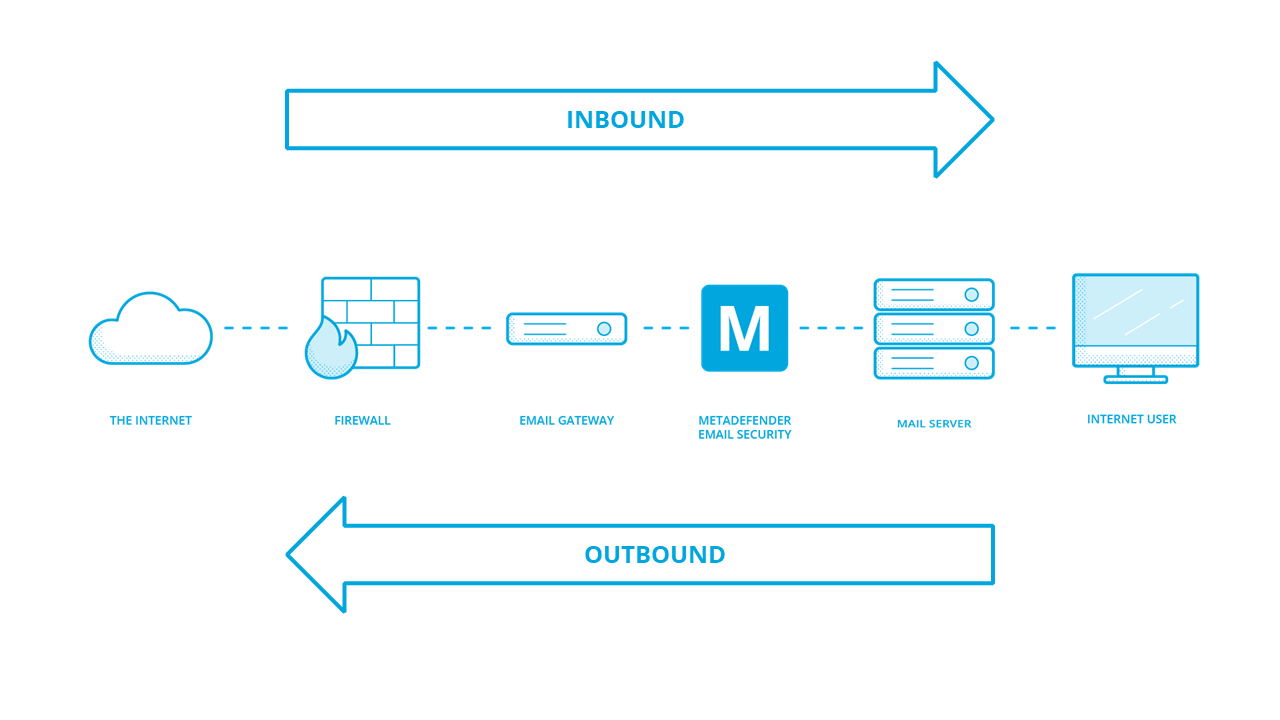
Metadefender Email Security traditional setup
Security rules overview
Security rules help to assign security policies to specific email messages.
A security rule consists of four parts:
-
General information
-
Email filter
-
Security policy definition
-
Rule order
General information
The following properties may be configured:
-
NAME: unique name of the rule
-
DESCRIPTION: optional, detailed description
-
DIRECTION: direction of the email messages this rule is intended to match.
From an email message it is hard –in some cases not even possible at all– to tell whether it was inbound or outbound. That is the reason why this setting only records what the administrator's intention was with the rule and it serves statistical purposes only.
There is no guarantee for example that an inbound rule will match inbound messages only.
On the 4.1 Dashboard page, however, MetaDefender Email Gateway Security will categorize an email as inbound or outbound based on the direction setting the matching rule has.
-
INBOUND: default, messages that are coming in to the organization
-
OUTBOUND: messages that are going out from the organization
-
Email filter
Based on the source(s), sender(s) and recipient(s), email filters select messages on which the assigned security policy will be applied. Email filters can be set up on the Filter tab while creating or editing a security rule.
Filter parts
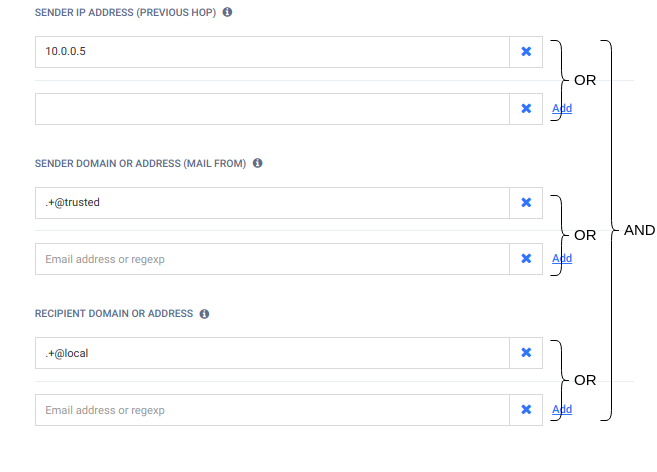
A filter may consist of three parts:
-
Sender IP address conditions
-
Sender domain or email address conditions
-
Recipient domain or email address conditions
There is AND relation among the above parts of the filter.
Sender IP address conditions
Sender IP addresses are the addresses of infrastructure elements in the deployment, from which MetaDefender Email Gateway Security is allowed to receive emails according to this rule.
In case of a traditional setup, for example, sender is the email gateway for inbound messages and the mail server for outbound messages.
|
Type |
IP address or subnet |
|
|
Match type |
EQUALS |
|
|
Examples |
IP |
10.0.0.1 |
|
Subnet |
10.0.0.0/24 |
|
There is OR relation among entries in sender IP address conditions.
Sender domain or email address conditions
Sender filter makes possible to apply security rule based on who sent the email. The value comes from the email envelope's MAIL FROM part.
Spoofing
When using this filter please be very aware of the fact that spoofing the sender of the email is a very easy task. A more secure way to use this filter would be for OUTBOUND emails only along with filtering to the sender IP.
|
Type |
|
|
Match type |
regular expression match |
|
Examples |
|
Note
Please note that the "." (dot) in a regular expression matches any character. This means .+@opswat.com can match test@opswat1com. If you want to match explicitly for a dot you should escape it like this: .+@opswat\.com
There is OR relation among the sender domain or email address conditions.
Recipient domain or email address conditions
Recipient conditions help to restrict email recipients allowed by the rule.
Recipient domain or email address conditions can also help to counter emails sent to invalid recipients; that do not even exist at an organization or among the partners, for example.
This kind of defense may protect against unnecessary overloads or even against malicious attacks.
In case of inbound directions rules usually allow organization internal e-mail addresses only. In case of outbound directions all e-mail addresses may be allowed.
|
Type |
|
|
Match type |
regular expression match |
|
Examples |
|
Note
Please note that the "." (dot) in a regular expression matches any character. This means .+@opswat.com can match test@opswat1com. If you want to match explicitly for a dot you should escape it like this: .+@opswat\.com
There is OR relation among the recipient domain or email address conditions.
Security policy
A security policy consists of the SCAN settings and the ACTIONS.
Scan settings
The scan policy can be set up on the SCAN tab while creating or editing a security rule.
The following options are available:
-
ALLOW SCAN: enable or disable scanning of requests. Default is enabled.
-
METADEFENDER CORE: MetaDefender Core type server profile to which emails are sent for scanning. Default is None.
-
SCAN TIMEOUT [IN SECONDS]: If a scan result is not available from the MetaDefender Core within this timeframe the scan will be cancelled. Default is 300 secs.
-
SCAN EMAIL BODY: Whether to scan the email body or not. Default is to enable scanning the body.
The attachments of the email will be scanned indifferent of this setting.
-
SCAN EMAIL HEADERS: Whether to scan the email headers or not. Default is to enable scanning the headers.
This function can help –for example– to prevent leaking sensitive information in email subjects.
When the header contains infection or sensitive data and if scanning email headers is enabled and the header is removed due to be blocked or sensitive (Policy > Security Rules / add/modify/ ACTIONS / HANDLING OF THE EMAIL is set to DELETE BLOCKED CONTENTS) then the email may be rendered with no sender, recipient, subject, etc. in the email client (as all this metadata is in headers):
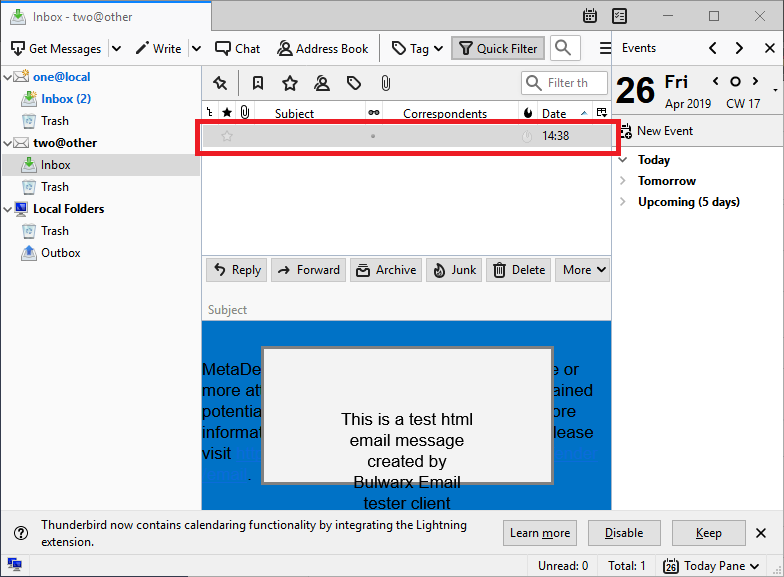
-
When scanning is disabled, all matching emails will be accepted.
Referenced Core rules may be changed or even deleted while they are still used by MetaDefender Email Gateway Security. For symptoms and solutions of such cases see section 148433311.
Actions
The actions policy define what should happen to a matching email message based on the scan outcome. Actions can be set up on the ACTIONS tab while creating or editing a security rule.
Scanning may have three kinds of outcome. The email message may either be
-
Blocked, or
-
Sanitized, or
-
Allowed.
An email message is blocked when any content in it is blocked by MetaDefender Core due to malware infection for example.
An email message is sanitized, when any attachment in it is sanitized by MetaDefender Core due to potentially harmful content for example.
An email message is allowed when there was no actual or potential problem found in it.
Description of the existing actions are the following:
-
DELETE BLOCKED ATTACHMENTS: all attachments blocked by MetaDefender Core are irreversibly deleted.
-
QUARANTINE ORIGINAL EMAIL: the whole email is blocked from further processing and sent to a specific container called quarantine. Messages can be recovered from the quarantine, for details see 4.3 Quarantine.
-
ADD DISCLAIMER: add the specified content to the end of the email message.
-
DISCLAIMER POSITION: Disclaimer can be added before or after the original content of an email
-
DISCLAIMER STYLE: A disclaimer style can be applied to emphasize content to the user (HTML only)
-
HTML: If the email is formatted as HTML then the content specified here will be appended. A HTML markup may be specified (e.g. HTML link, inline CSS) and it will be rendered properly in the resulting email message.
Example<p>MetaDefender Email Gateway Security scanned this email to detect any potentially maliciousembedded objects. For more information on MetaDefender Email Gateway Security, please visit<ahref="https://www.opswat.com/products/metadefender/email-security">https://www.opswat.com/products/metadefender/email-security</a>.</p>Internal and external CSS
Using internal style sheets (defined by using the < style > tag within the <head> area of the HTML document ) or external CSS (a file that contains only CSS code and is saved usually with a . css file extension, then this CSS file is referenced in the <head> area of the document using the <link> (instead of <style> )) may give unexpected results.
-
PLAIN TEXT: If the email is plain text or formatted as Rich Text Format (RTF) then the text specified here will be appended with no formatting.
-
-
ADD THE FOLLOWING HEADERS: the specified headers will be added to the internet headers section of the email message. Click the ADD ROW button to add a new header to the list.
Actions for emails with blocked contents
The following actions are available for emails with blocked contents:
|
Action |
QUARANTINE ORIGINAL EMAIL |
HANDLING OF THE EMAIL |
ADD DISCLAIMER |
DISCLAIMER POSITION |
HTML |
PLAIN TEXT |
ADD THE FOLLOWING HEADERS |
||||||||
|
Default |
ON |
BLOCK EMAIL
|
ON |
AFTER CONTENT |
<p>MetaDefender Email Gateway Security blocked this email due to malicious embedded objects. For more information on MetaDefender Email Gateway Security, please visit <a href="https://www.opswat.com/products/metadefender/email-security">https://www.opswat.com/products/metadefender/email-security</a>.</p> |
MetaDefender Email Gateway Security blocked this email due to malicious embedded objects. For more information on MetaDefender Email Gateway Security, please visit https://www.opswat.com/products/metadefender/email-security. |
None |
||||||||
|
Notes |
|
|
|
|
|
|
|
Customizing notifications
Restricting blocked emails causing notifications
You can customize what range of blocked emails to produce notification emails.
Default
By default Email Gateway Security will send a notification for each blocked email.
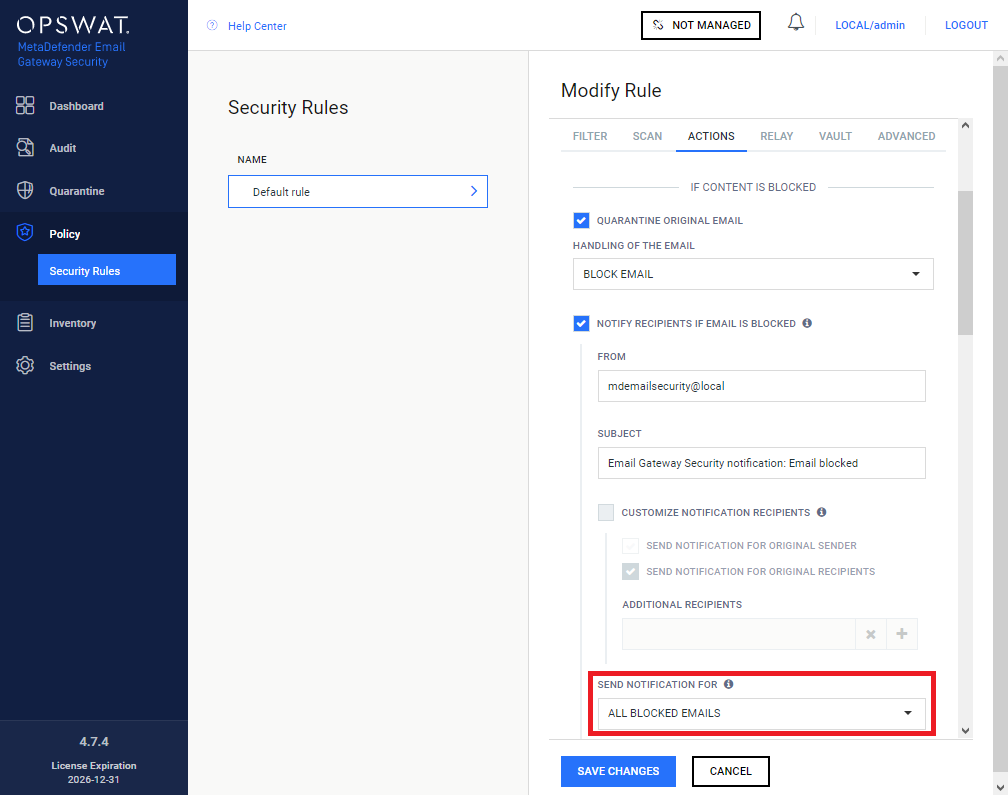
To configure what range of blocked emails to cause a notification email to be sent, go to Policy > Security Rules / add/modify / ACTIONS / NOTIFY RECIPIENTS IF EMAIL IS BLOCKED / SEND NOTIFICATION FOR and from the drop down list select your preference.
The following options are currently available:
-
ALL BLOCKED EMAILS: Email Gateway Security will send a notification email for each blocked email (including emails with password protected attachments).
-
ONLY EMAILS WITH PASSWORD PROTECTED ATTACHMENTS: notification emails are sent for emails with password protected attachments only.
Customizing notification recipients
You can customize the recipients of notification emails. To enable the customization the CUSTOMIZE NOTIFICATION RECIPIENTS should be enabled.
-
SEND NOTIFICATION FOR ORIGINAL SENDER: When this option is enabled, the sender of the original email will receive the notification email.
Example
Enabling this option will allow the sender to provide the password (for a password protected document or archive) so that she can have the email scanned before it is sent out the organization.
-
SEND NOTIFICATION FOR ORIGINAL RECIPIENTS: When this option is enabled every recipient of the original email will receive the notification email. If disabled only the additional recipients will receive the notification email.
-
ADDITIONAL RECIPIENTS: You can add additional recipients who should also receive the notification emails. This could be an administrator or a notification email parser system for example.
There is at least one recipient is needed for the notification emails, so disabling the notification sending for original recipients without an additional recipient is not allowed.
Options for emails with blocked contents if the blocked content is a password protected attachments
|
Option |
ADD DISCLAIMER FOR ENCRYPTED ATTACHMENTS |
DISCLAIMER POSITION |
HTML |
PLAIN TEXT |
SEND UNIQUE RESCAN LINK FOR EVERY RECIPIENT |
|
Default |
OFF |
AFTER CONTENT |
<p>MetaDefender Email Gateway Security has removed <strong>password protected attachment(s)</strong> in this email. Please click <strong><a href="%[]rescan_link_url[:]%">here</a></strong> to rescan the email and deliver all contents. For more information on MetaDefender Email Gateway Security, please visit <a href="https://www.opswat.com/products/metadefender/email">https://www.opswat.com/products/metadefender/email.> |
MetaDefender Email Gateway Security has removed password protected attachment(s) in this email. Please click %[]rescan_link_url[Your administrator did not set a public server address for rescan]% to rescan the email and deliver all contents. For more information on MetaDefender Email Gateway Security, please visit https://www.opswat.com/products/metadefender/email. |
OFF |
|
Notes |
|
|
%[]rescan_link_expiry[]% and %[]rescan_link_url[]% will be replaced by the RESCAN LINK AVAILABILITY and PUBLIC SERVER ADDRESS values from 3.4 General settings. If the PUBLIC SERVER ADDRESS is not set then the "Your administrator did not set a public server address for rescan" text will be displayed instead. For further details about disclaimer variables see 4.2.1 Disclaimer variables. |
%[]rescan_link_expiry[]% and %[]rescan_link_url[]% will be replaced by the RESCAN LINK AVAILABILITY and PUBLIC SERVER ADDRESS values from 3.4 General settings. If the PUBLIC SERVER ADDRESS is not set then the "Your administrator did not set a public server address for rescan" text will be displayed instead. For further details about disclaimer variables see 4.2.1 Disclaimer variables. |
When this option is enabled every recipient will receive a unique rescan link to provide password(s) for the encrypted attachments. Providing the correct password(s) through a unique link means that only the recipients who provided the password(s) will receive the attachment(s) and it won't be automatically sent to others. If the password is provided by the administrator through the Web Management Console then the behavior is not changed and every recipient will receive the attachments. |
Actions for emails with sanitized contents
The following actions are available for emails with sanitized contents:
|
Action |
QUARANTINE ORIGINAL EMAIL |
ADD DISCLAIMER |
DISCLAIMER POSITION |
HTML |
PLAIN TEXT |
ADD THE FOLLOWING HEADERS |
|
Default |
ON |
ON |
AFTER CONTENT |
<p>MetaDefender Email Gateway Security sanitized this email due to potentially malicious embedded objects. For more information on MetaDefender Email Gateway Security, please visit <a href="https://www.opswat.com/products/metadefender/email-security">https://www.opswat.com/products/metadefender/email-security</a>.</p> |
MetaDefender Email Gateway Security sanitized this email due to potentially malicious embedded objects. For more information on MetaDefender Email Gateway Security, please visit https://www.opswat.com/products/metadefender/email-security. |
None |
Actions for allowed emails
The following actions are available for allowed emails:
|
Action |
ADD DISCLAIMER |
DISCLAIMER POSITION |
HTML |
PLAIN TEXT |
ADD THE FOLLOWING HEADERS |
|
Default |
OFF |
AFTER CONTENT |
<p>MetaDefender Email Gateway Security scanned this email to detect any potentially malicious embedded objects. For more information on MetaDefender Email Gateway Security, please visit <a href="https://www.opswat.com/products/metadefender/email-security">https://www.opswat.com/products/metadefender/email-security</a>.</p> |
MetaDefender Email Gateway Security scanned this email to detect any potentially malicious embedded objects. For more information on MetaDefender Email Gateway Security, please visit https://www.opswat.com/products/metadefender/email-security. |
None |
Relay
Exchange Server mode
Relay is not available in case of on-site Exchange Server deployments. The reason is that in case of Exchange mode emails are sent back to the Exchange Server at the end of processing.
Relay specifies where to send next an e-mail message when it is not blocked (it is not scanned; it is allowed, sanitized, released or forwarded). As a closing act of processing the email message it is tried to be forwarded to the SMTP servers specified by the relay.
Relay can be set up on the Relay tab while creating or editing a security rule.
Relay itself is an SMTP type server profile. For details about server profiles see 3.7 Server profiles.
In case of a traditional setup, for example, relay is the email gateway for outbound messages and the mail server for inbound messages.
Resending
If the email is failed to be sent to any of the SMTP server defined by the relay server profile, then sending is retried according to the settings documented in 3.4 General settings.
If sending the email keeps failing even after the retries, then MetaDefender Email Gateway Security gives up.
In case of permanent failure the email message remains in the queue, it will not be deleted. As a consequence permanently failing messages may accumulate on the MetaDefender Email Gateway Security server consuming disk space.
Vault
MetaDefender Email Gateway Security can be integrated with MetaDefender Vault which makes possible to upload attachments to MetaDefender Vault during processing emails on a security rule basis. For more details and possibilities please check 4.9 Integration with MetaDefender Vault.
Advanced scan settings
The advanced scan settings policy define certain exceptions from the default behavior. Advanced scan settings can be set up on the ADVANCED tab while creating or editing a security rule.
The following options are available:
-
OVERRIDE SMTP RESULTS allows overriding default behavior in the following cases
-
SMTP SERVER NOT RESPONDING: SMTP server is not reachable or some other connection error occured when trying to reach it; default: Retry
-
SMTP PERMANENT FAILURE: SMTP server responded with 5xx error code (e.g. 550 mailbox unavailable); default: Retry
-
-
OVERRIDE SANITIZATION BEHAVIOR allows overriding default behavior in the following cases
-
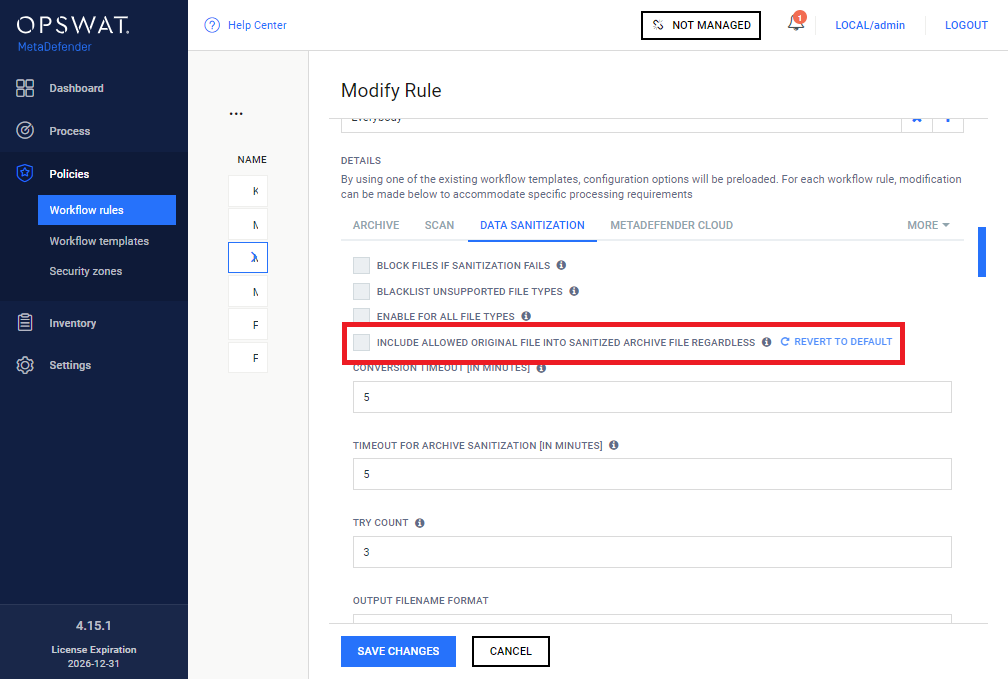
SKIP PARTIAL SANITIZATIONS: Do not replace partially sanitized archives in email attachments, handle them as if there was no sanitization at all for the archive file.
Core 4.15.1 required
This feature requires MetaDefender Core version 4.15.1.
For this feature to work, Policies > Workflow rules / add/modify / DATA SANITIZATION / INCLUDE ALLOWED ORIGINAL FILE INTO SANITIZED ARCHIVE FILE REGARDLESS must be disabled for the Core side rule, that is in use in the Email Gateway Security side rule.
-
SEND SANITIZED VERSION OF BLOCKED FILES: when this option is enabled and the 148433311 is set to "DELETE BLOCKED CONTENTS" then instead of deleting the blocked file Email Gateway Security will send the sanitized version of that file if available. If the sanitized version of the blocked file is not available the file will be deleted.
-
SEND ORIGINAL FILE IF THE SANITIZATION FAILED FOR makes possible to receive the original file if the sanitization fails for the given cases
-
NONE: Emails with sanitization failure will be blocked or the files whose sanitization failed will be deleted for every type of file; this is the default behavior
-
PASSWORD PROTECTED DOCUMENTS: Emails with sanitization failure will be allowed or the files whose sanitization failed won't be deleted if the original file was identified as a "Password Protected Document". The email will still be blocked if there is an other issue like an infected file or a sanitization failure for a non "Password Protected Document".
-
EVERY ALLOWED FILE: Emails with sanitization failure will be allowed or the files whose sanitization failed won't be deleted if the original file was not blocked by Core. The email will still be blocked if there is an other issue like an infected file.
-
-
ADD SANITIZATION FAILURE DISCLAIMER: Add this disclaimer to the email if there is a sanitization failure.
-
-
DO NOT MODIFY S/MIME AND PGP SIGNED EMAILS allows skipping the modification of emails which are signed; default: Enabled. With this option enabled the digital signature of the email can remain valid. For more information check 4.8 Support for signed emails.
-
OVERRIDE ERROR HANDLING BEHAVIOR allows overriding default error handling behavior in the following cases
-
CORE UNREACHABLE: no network connection to Core; default: Bypass if all retry fail
-
CORE BUSY: Core actively refuses scanning due to overload; default: Bypass if all retry fail
-
SCAN TIMEOUT: scanning timeouts on Core; default: Bypass if all retry fail
-
CORE PROCESSING FAILED: Core fails to scan; default: Bypass if all retry fail
-
NOT SCANNED RESULT FROM CORE: A 'Not scanned' result received from Core; default: Bypass if all retry fail
-
EMAIL MODIFICATION FAILURE: Failure to apply expected modification to email: Retry
-
-
BYPASS HEADERS: the specified headers will be added to the internet headers section of the email messages that bypassed scanning ( Bypass if all retry fail ). Click the ADD ROW button to add a new header to the list.
-
BYPASS DISCLAIMER
-
DISCLAIMER POSITION: the position of the disclaimer; default: BEFORE CONTENT
-
DISCLAIMER STYLE: A disclaimer style can be applied to emphasize content to the user (HTML only)
-
HTML: the specified disclaimer will be added to the HTML formatted email messages that bypassed scanning ( Bypass if all retry fail ).
-
PLAIN TEXT: the specified disclaimer will be added to the plain text and RTF formatted email messages that bypassed scanning ( Bypass if all retry fail ).
-
Rule order
Several security rules can be created that may target different messages from different sources going to different recipients. However, care must be taken how these rules are set up and ordered, as there is a 148433311 and a 148433311.
Specific rules should come first while generic rules should go at last.
Order of evaluation of security rules for a match
First match policy
If there are more matching rules in the system, then the email message will be accepted or rejected according to the security policy of the first matching rule in the list.
No match policy
If there is no matching rule in the system (or no rule at all), then the email message will be rejected.
There are no default security rules in MetaDefender Email Gateway Security. As a consequence all email messages are blocked by default.
Deleting all security rules from the system results all email messages being blocked.
Security Rule Management
The Security Rule Management screen lists the existing security rules in the system.

Functions
Besides listing existing security rules the Security Rule Management screen provides the following functions:
-
Add new security rule
-
Clone an existing security rule
-
Modify (and view) existing security rule's properties
-
Delete existing security rule
-
Reorder existing security rule