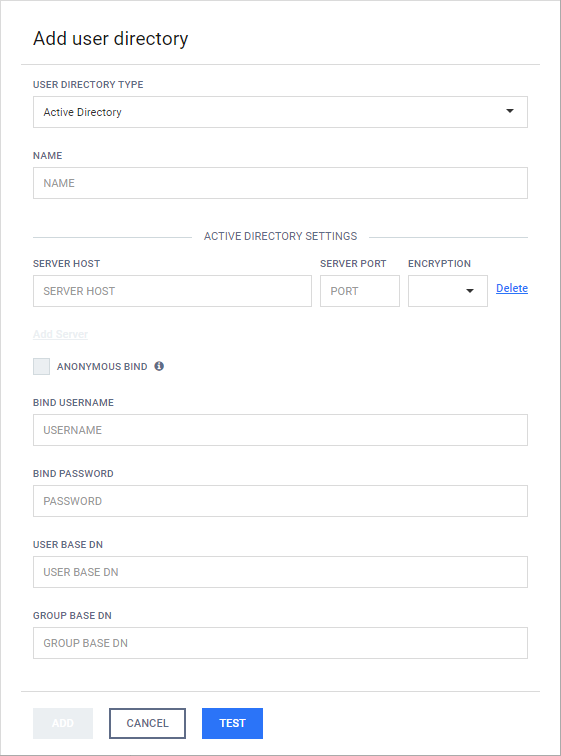
3.2.3. Active Directory attributes
This page contains tips on how to obtain the BIND USERNAME, the USER BASE DN and GROUP BASE DN attributes when creating an Active Directory type user directory.
Normally a domain administrator should provide these values.
All three attributes must be expressed using a valid LDAP syntax.
Bind username
Normally a domain administrator should provide these values, however there is a way to get the BIND USERNAME as an LDAP DN, that is needed for the product to do searches in the directory information tree, and it is as follows:
-
Log on to a Windows server machine that has connectivity to the Active Directory
-
Choose a user that is intended for this purpose (ie: has rights to do searches in the tree)
-
Open a Command window with elevated rights (Run as Administrator)
-
Assuming example.com as domain and John Smith with account name john.smith as the user, type the following:
> dsquery user domainroot -samid john.smithor
> dsquery user domainroot -name John SmithThe commands above will return the correct DN for the user in question. The DN should look something like this:
CN=John Smith,OU=People,OU=Engineering,DC=example,DC=comPlease note, the actual user DN will not look exactly like the above example, but will depend on the structure of the underlying directory information tree in the Active Directory server.
On non-server Windows machines the dsquery command can be obtained with installing the Remote Server Administration Tools (RSAT).
User base and group base DN
Once the bind user DN is obtained, an easy way to get the DNs for the user and group searches is by taking all the DC parts of the user DN and leaving the rest out, which results in the following DN:
DC=example,DC=com
Please note that using only DC components for the user/group DNs may result in searches to be executed from the top of the directory information tree and potentially slow down AD server responses a lot and thus have an impact on the MetaDefender product's password validation. The rule of thumb here is that the more specific the user/group DN the faster the server response.
Taking the above example into consideration: a user search DN of "OU=People,OU=Engineering,DC=example,DC=com" could potentially result in much faster server response than "DC=example,DC=com" and should be preferred assuming all users reside under "OU=People,OU=Engineering,DC=example,DC=com" in the directory information tree.
Please also note that users and groups may reside in different parts of the directory information tree, as a consequence applying the same, more specific DN both as USER BASE DN and GROUP BASE DN may cause the MetaDefender product to not find group accounts in the directory information tree. So these DNs should be chosen carefully.