1.2. Upgrading From Old Versions
Upgrading to the newer version
In order to perform an upgrade to the latest version or a newer version, please follow the steps described in Installing MetaDefender Vault Using the Install Wizard in order to upgrade the product.
Note: Uninstalling MetaDefender Vault will not cause any data or settings loss including files, configuration, and license. If you want to do a clean uninstall and install, follow Clean uninstall of MetaDefender Vault.
Upgrading from Vault 1.3.6 or lower to the latest version
From version 1.3.7 and onward, Vault will be using NGINX as the underlying web server.
Although the way users interact with the system remains largely unchanged, there are a couple of differences to be aware of.
-
The REST API and User Interface ports can no longer physically share the same value (REST API will be auto re-assigned to the first free port starting from 8000 upward).
-
All REST calls will now be made to the web client's port and NGINX will reroute them to the appropriate destination.
-
It is no longer valid to provide a certificate hash, in case of TLS/SSL settings.
-
The paths to the actual certificate and private key have to be provided. In the case of password-protected certificates, the path to the file containing the passwords is also necessary.
The migration to NGINX will be handled by the installer.
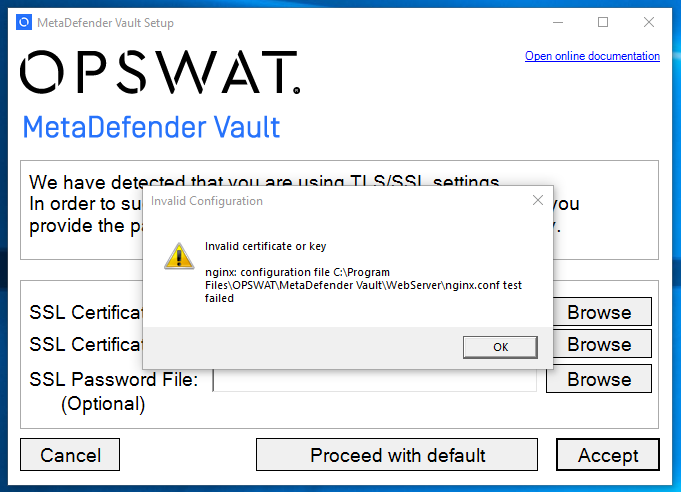
During the upgrade process, if TLS/SSL settings are detected, a pop-up window will appear, asking for the user to provide the paths to the:
-
SSL certificate
-
SSL certificate private key
-
(Optional) The path to a text file containing the password for the protected certificate
The user can opt to reset to factory defaults by clicking Proceed with default (in which case all TLS/SSL settings will be lost).
When pressing the Accept button, a check will be made to validate the contents before continuing with the installation. Data is considered valid if it fulfills the following criteria:
-
SSL certificate must be provided in the .pem or .crt formats.
-
SSL certificate private key must be provided in the .pem or .key formats.
-
The private key must be applicable to the given certificate.
-
In case the certificate is password protected, then a text file containing the password must also be provided.
In case the input data is invalid, a warning will be presented. Click OK and try again.
If everything is successful then the following screen will be presented: