6.5. Version 5.1.0
5.1.0 MetaDefender Email Gateway Security release |
|
|
September 21, 2020 |
MetaDefender Email Gateway Security 5.1.0 is a feature release focusing on the new anti-spam and anti-phishing capability of the product. |
New & improved |
|
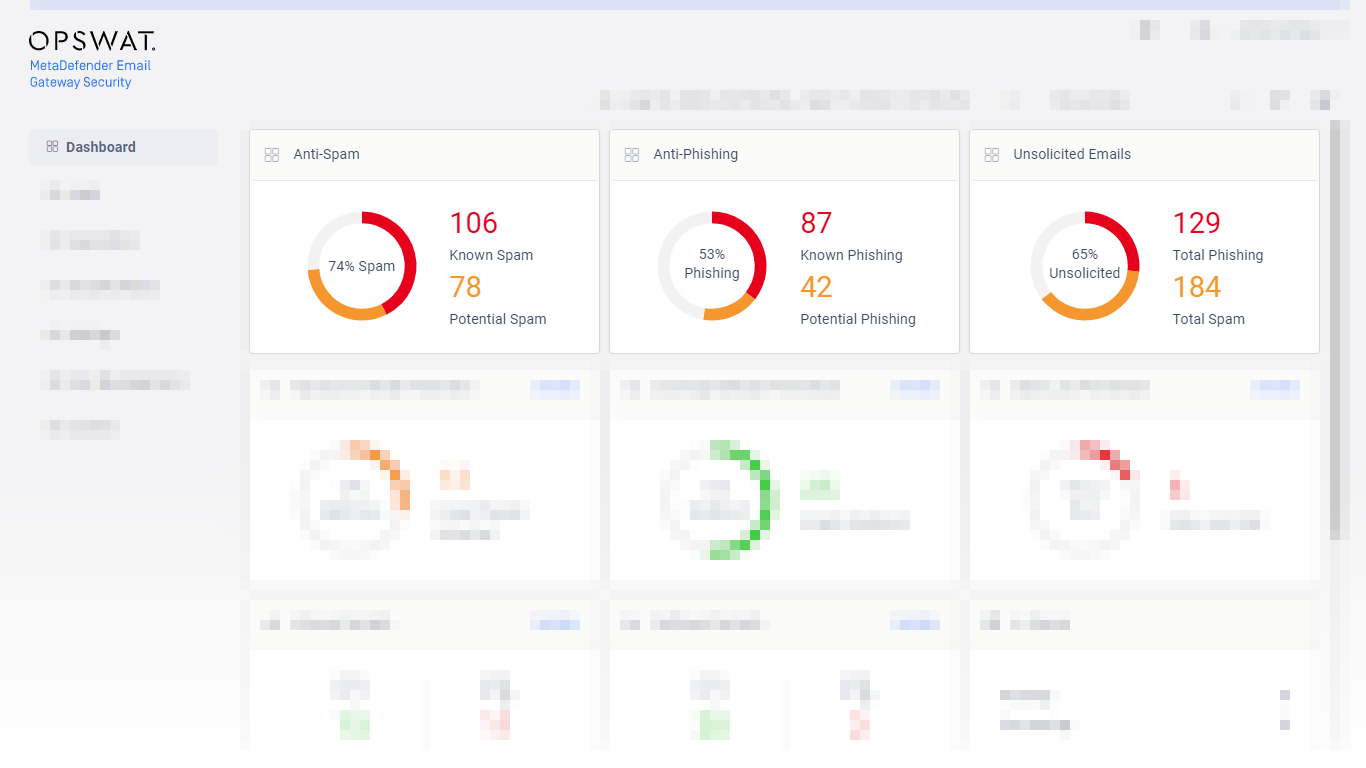
Anti-spam and anti-phishing capability |
As a great step forward, Email Gateway Security 5.1.0 provides anti-spam and anti-phishing capabilities. Integrating one of the best solutions, we have 99.7% spam-cacth-rate with 0.00% false positives and 98.2% phishing-catch-rate. For details about configuring and operating Email Gateway Security’s anti-spam and anti-phishing, see 4.4. Policy and 5.6. Phishing and spam respectively. |
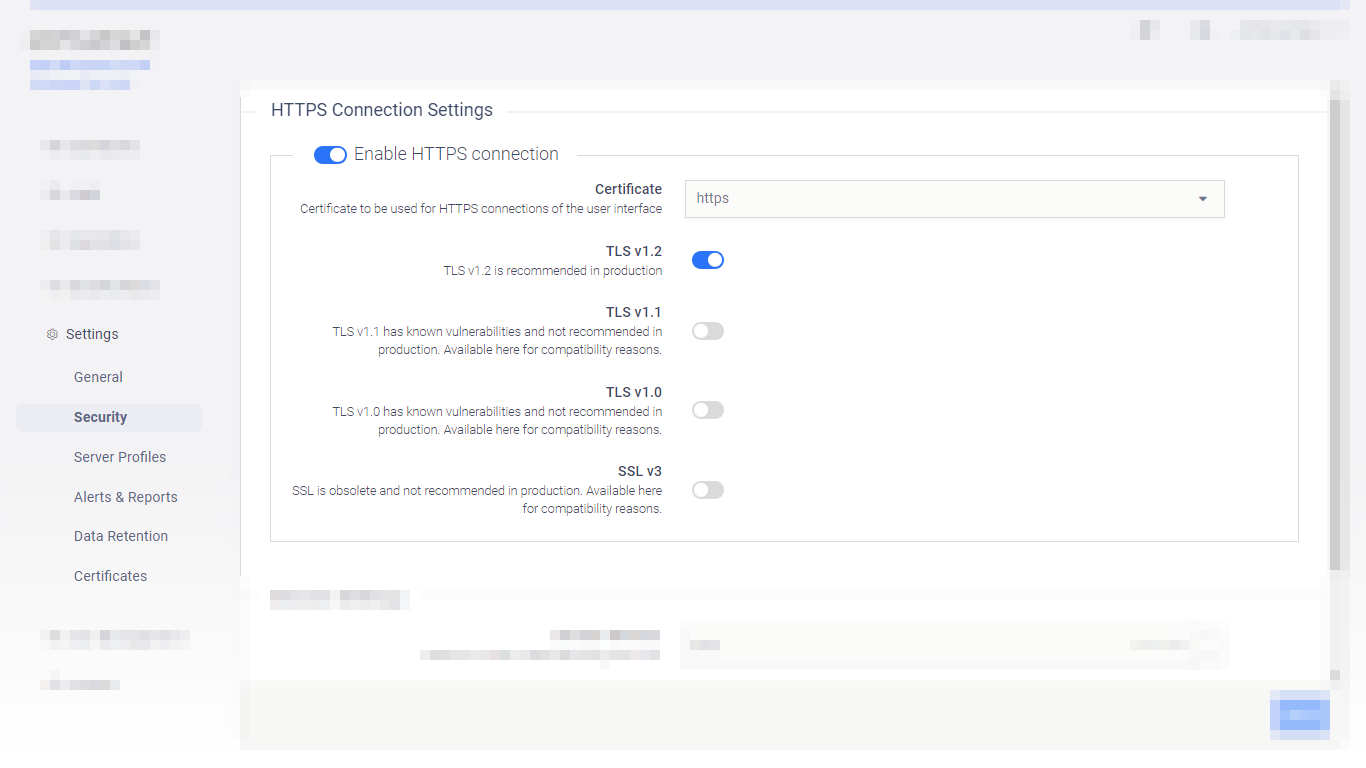
Simplified TLS configuration for the UI |
It is now supported to configure TLS for the web management console from the GUI. For details see 4.2. Transport Layer Security. |
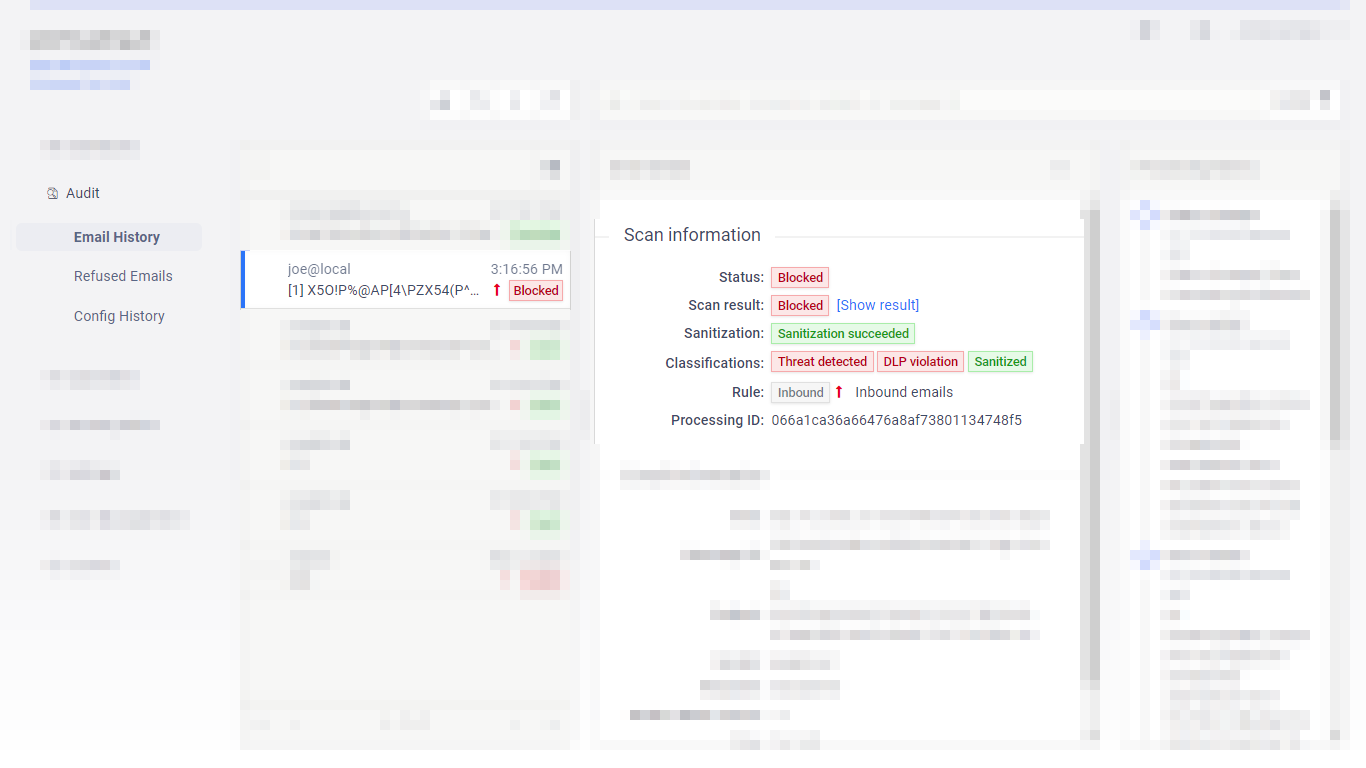
Classifications in history & quarantine |
To better reflect the risk level associated to a certain email and for easier understanding what potential risks an email carries, Email Gateway Security introduced classifications of emails. For details see 5.10 Email classifications. |
Rotation of Nginx log files |
To save disk space, it is supported now to rotate Nginx logs. For details see 4.1. Registry configuration. |
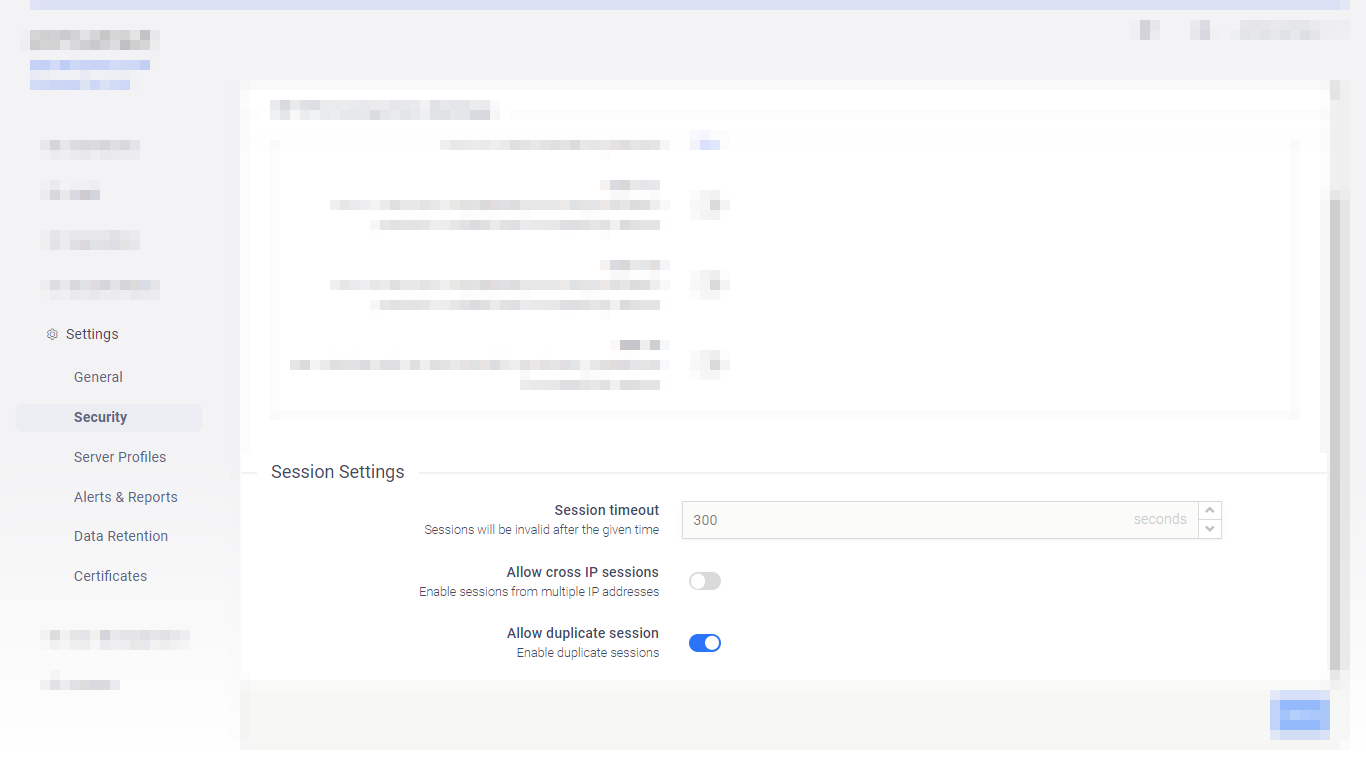
Session timeout settings in the UI |
|
Propagate TLS configuration for the UI |
When TLS is enabled for the Email Gateway Security bundle edition, then this setting is now propagated to the bundled MetaDefender Core instance’s UI, too. The configuration in the server profile is automatically upgraded from http to https. For details about editions see 1. Licensing. For details about TLS configuration see 4.2. Transport Layer Security. For details about server profiles see 4.6. Server profiles. |
Fixed |
|
Public rescan over TLS enabled port |
When TLS was enabled for the web management console, the TLS enablement was not propagated to the public rescan port and as a consequence the public rescan page remained on clear text HTTP. |