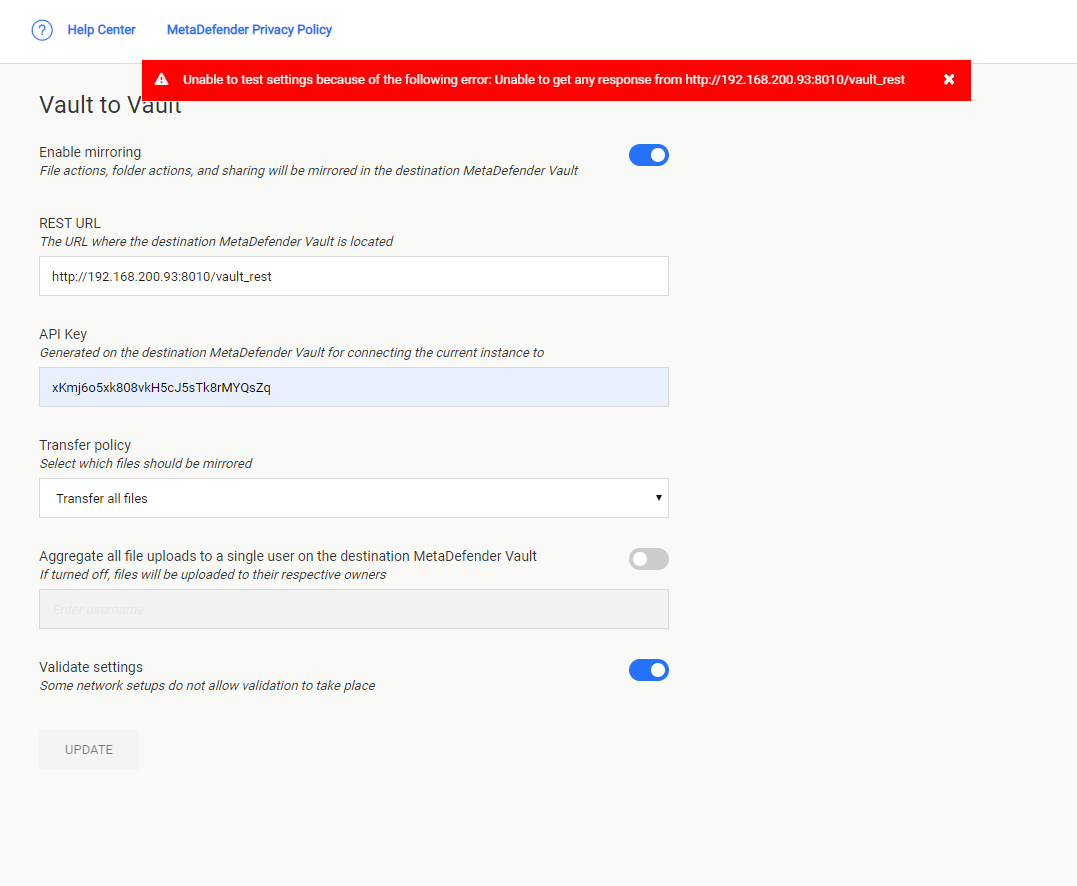
This feature makes it possible to transfer files between different networks using a secure and controlled connection. When enabled, all file and folder operations will be sent from the primary Vault to the destination Vault server.
A policy can be specified to choose if every file should be transferred or only the ones that are allowed by MetaDefender Core.
Supported operations
The supported file and folder actions can be seen in the table below:
|
Operation
|
File
|
Folder
|
|
Upload (Create)
|

|

|
|
Share
|

|

|
|
Move
|

|

|
|
Rename
|

|

|
|
Delete
|

|

|
Note
Guest user creation is also supported. Please keep in mind that the other user manipulation actions (update, delete, etc.) are not implemented.
The functionality can be configured by navigating to the Settings page and then choose Vault to Vault
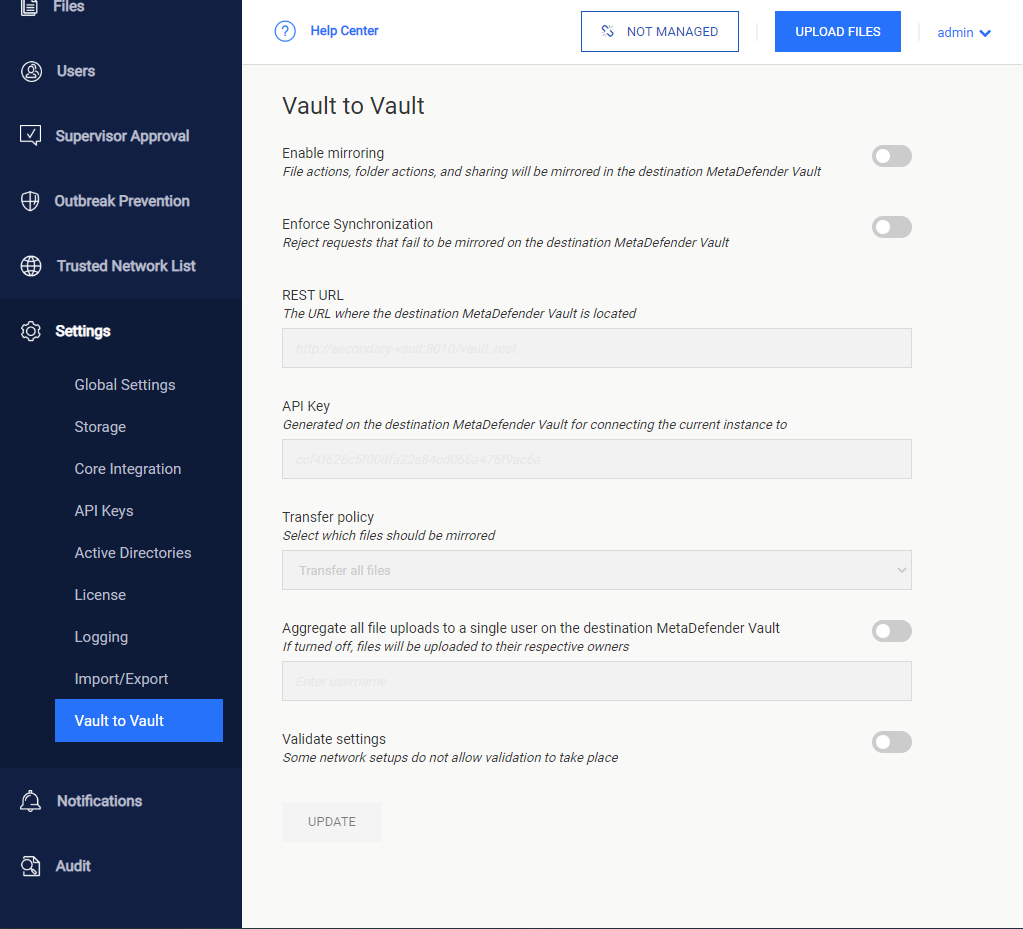
By default the feature is disabled. In order to enable the feature and proceed to configuration, the user must switch on "Enable mirroring".
In order to connect with an upstream Vault instance, the following steps must be performed:
-
Provide the REST URL of the upstream Vault instance.
The URL must have the following format <schema>://<address>:<port>/[vault_rest].
-
Log in with an administrator account on the second Vault and generate an API key.
The generated API key will be used to authorize requests from the first vault.
-
Enforce Synchronization: by default this option is disabled, turn on if you want to show bad requests when there is any unsynchronization between the two Vaults 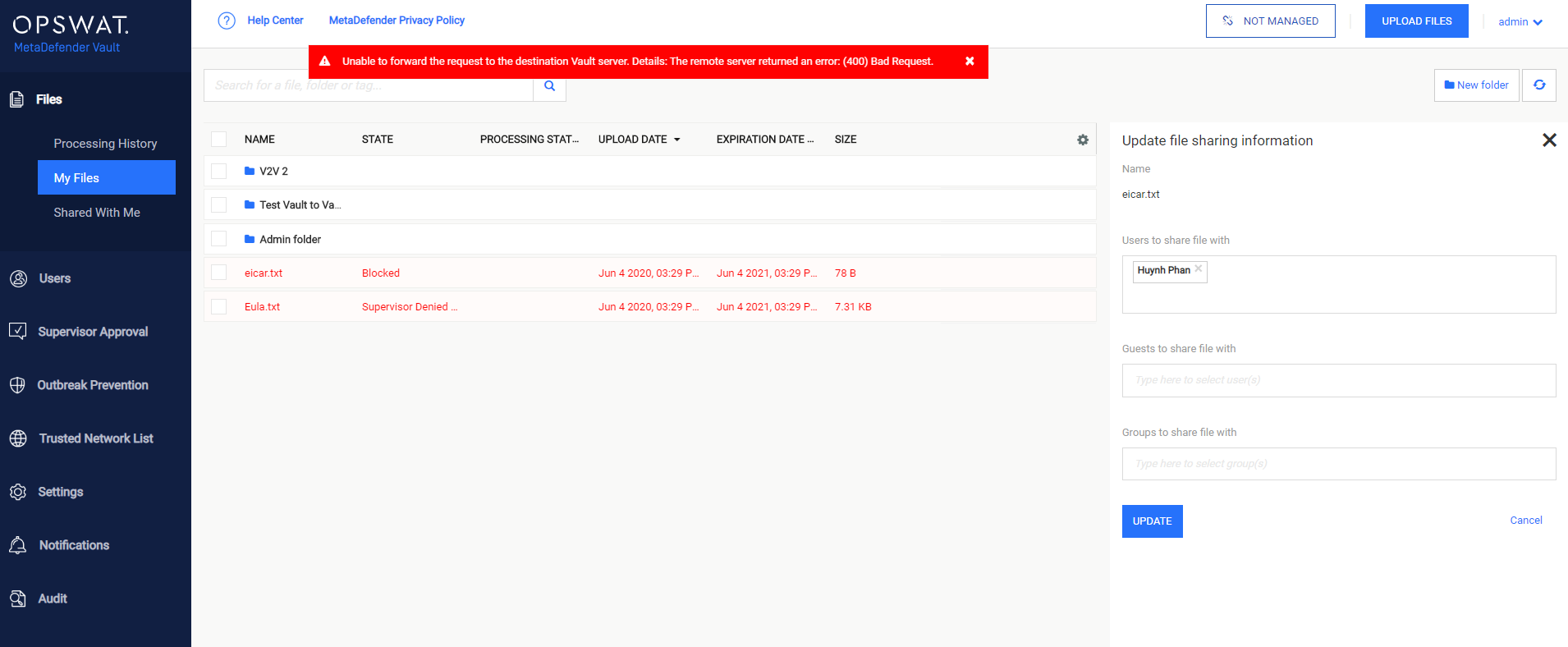
-
Transfer policy configuration specified which files should be transferred:
-
Transfer all files
-
Transfer only allowed files
-
(Optional) Aggregate all file/folder actions to a single user.
All forwarded actions will be interpreted as if the impersonated user requested them.
For example, files will be uploaded to the impersonated user's account regardless of the user who initiated the actions on the first vault.
The impersonated user must exist on both Vault instances.
This implies that both instances must integrate with the same Active Directory or have the same local accounts created.
If the impersonated user does not exist then all requests will be done on behalf of the user which generated the API key.
-
(Optional) Validate settings
If enabled, an initial connection test is performed to ensure that the settings are valid.
If disabled, no attempt is made to validate the configuration. This can be useful when responses from the other network are not allowed.
In the case, a data diode is deployed between the two Vault servers it may be impossible to receive a response from the second Vault. The validation feature will have to be manually turned off in order for the setup to work.