Modules
Engine type details
Under the Modules menu all the installed engines are listed with their details such as
-
Type of engine. Possible types are
-
Anti-malware engine
-
Archive engine
-
Data Loss Prevention engine
-
Data sanitization engine
-
Filetype detection engine
-
Utility engine
-
Vulnerability detection engine
-
-
Elapsed time since last update
-
Proportion of active and non-active engines of a particular type
-
Engine version
-
Version of database the engine is currently using
-
Engine status (Active/Non-Active)
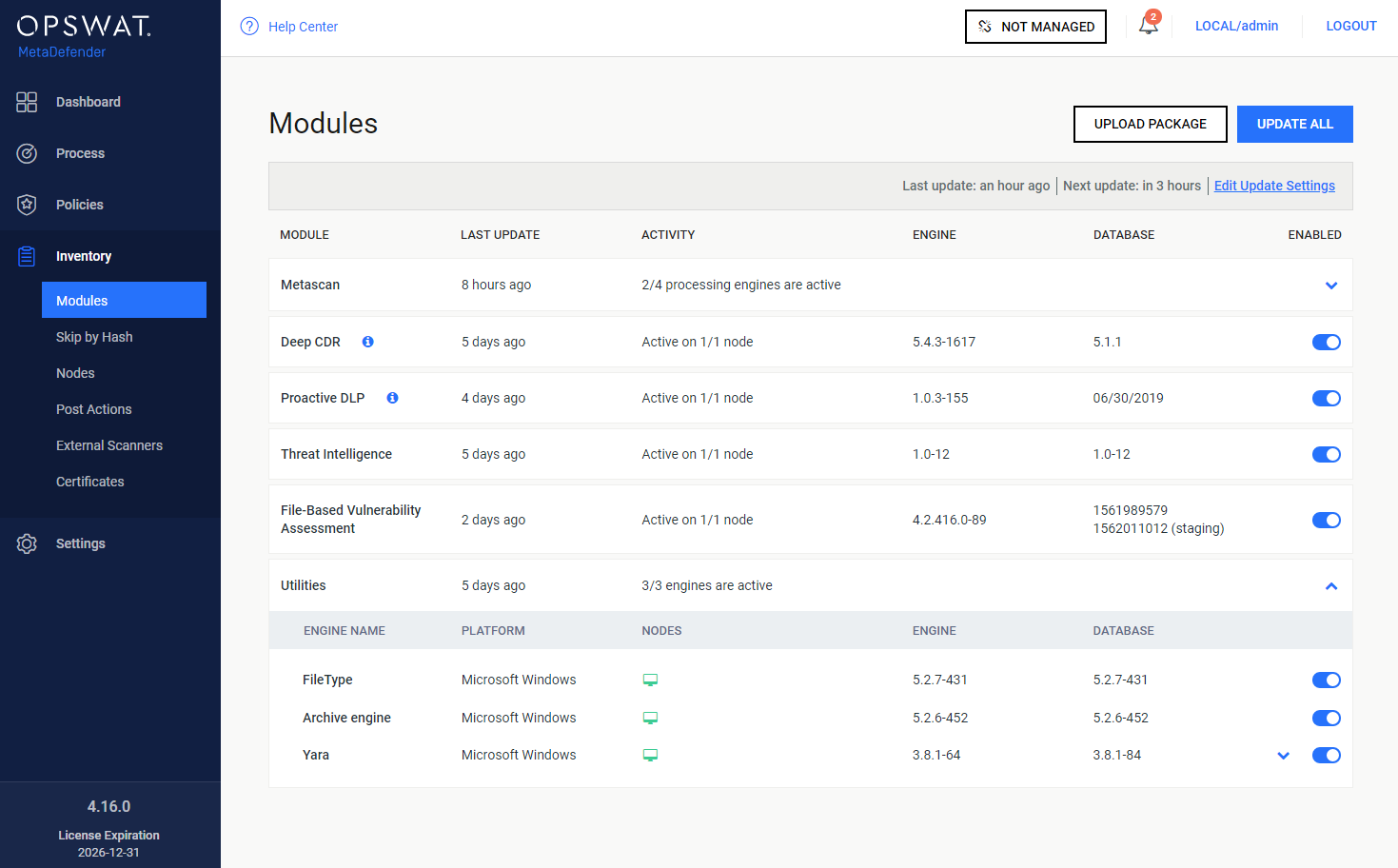
Engines can be disabled (and re-enabled afterwards) by clicking on the switch at the end of the line that belongs to that particular engine. When an engine is disabled neither the engine nor the corresponding database package is updated and it will be removed from every node.
Pin & Unpin engines (for auto-update prevention)
Engine and its database can be pinned to prevent it from being applied new updates when you allow auto update on Core. To pin it, just mouse over desired engine / database, and there you will see a "pin" icon
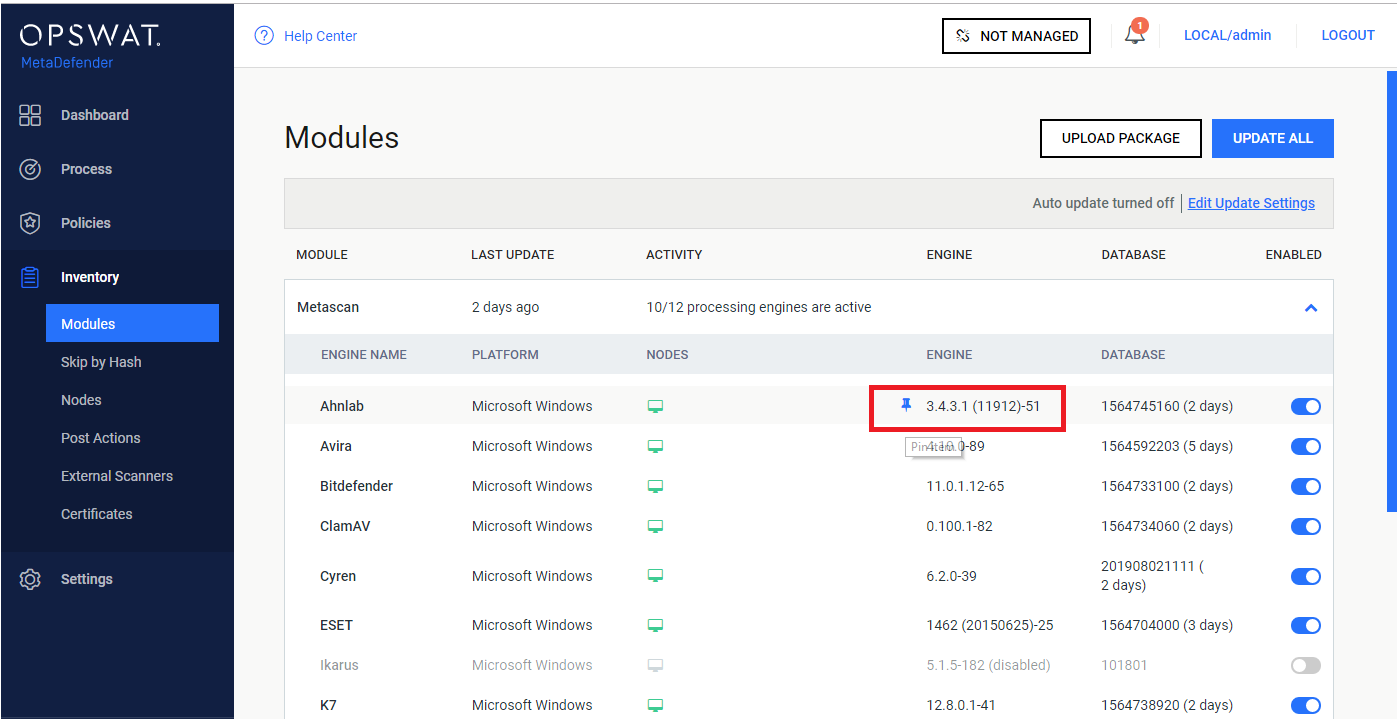
When pinned successfully, you are supposed to see a pin icon right next to that affected item indicating that:
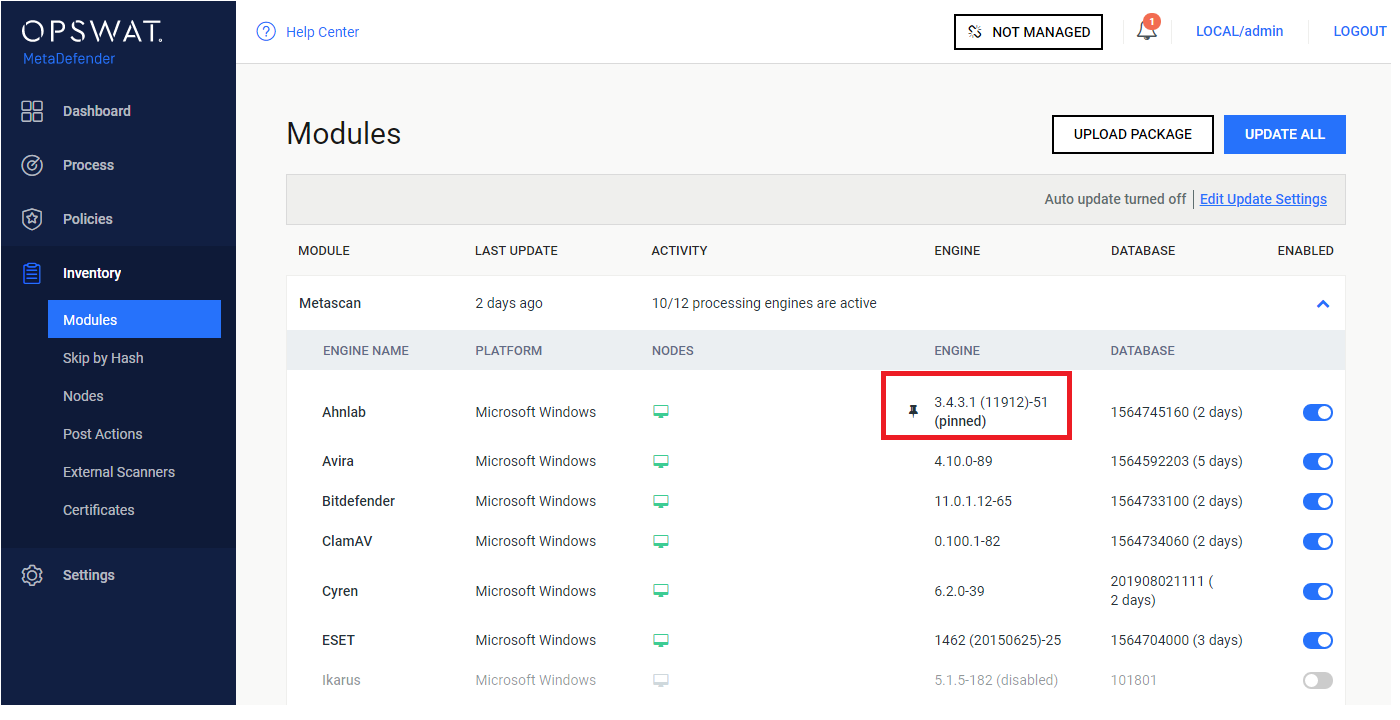
Some notes:
-
You can pin engine and database individually on same engine
-
When pinned, that means no auto update can be applied on that part (engine / database), even when user triggers "Update All" button
To allow applying auto update back, just click on pinned icon again.
Manual updates
To manually trigger update of scan engine and database packages, click on the Update now button.
To provide engine or database packages on your own, select the Upload package option.
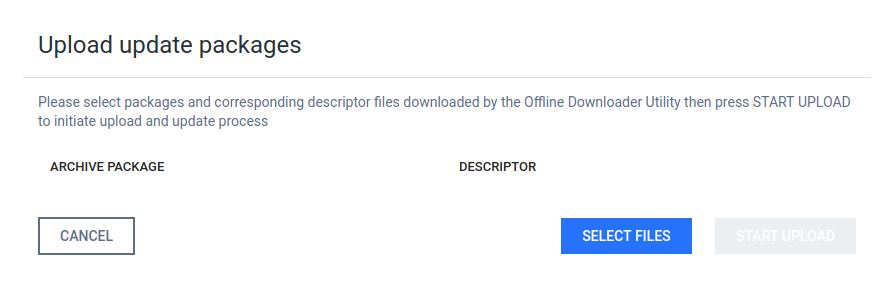
Upload packages
The package should be a ZIP and the descriptor YML file, which can be downloaded with the Update Downloader. Multiple files can be selected.
Engine or database versions that have ever been used on a system won't be accepted as updates.
Configuring engines
Some engines can be configured by using Advanced Engine Configuration. Hover mouse pointer over the line related to the engine to be configured and then click on that line, then hit Settings. The edit page is displayed.
Choose your desired configurations and click Save Settings, then Close.
Available options
|
Scan engine |
Configuration |
Note |
|
ClamAV |
[engine]
|
max_file_size: Setting it too high may result in severe damage to the system. Make sure you have enough free memory. Setting to 0 to disable this limit. max_scan_size: The maximum amount of data to scan for each container file. Certain files (e.g. documents, archives, etc.) may contain other files inside. This options ensure safe processing of this kind of data. Setting it too high may result in severe damage to the system. Make sure you have enough free memory. Setting to 0 to disable this limit. deep_scan: 0 - Do not scan the whole file if it is a big file enable_pcre : only available on the Linux version, enable this configuration will increase the detection rate but may affect performance |
|
Avira |
[engine] |
heuristic_scan: 0 - Disable heuristic detection. enable_pup_scan: only available on Windows |
|
ESET |
[engine] |
|
|
Ahnlab |
[engine] |
enable_pup_scan: only available on Windows |
|
BitDefender |
[engine] |
|
|
CYREN |
[engine] |
|
|
QuickHeal |
[engine] |
|
|
Vir.IT eXplorer |
[engine] |
|
|
TotalDefense |
[engine] |
|
|
F-Prot |
[engine] |
heuristic_scan: 0 - No heuristics. |
|
Ikarus |
[engine] |
|
|
K7 |
[engine] |
|
|
TACHYON |
[engine] |
|
|
Emsisoft |
[engine] |
extract_archive will not work if enable_bd_module is disabled |
|
Kaspersky |
[engine] |
heuristic_scan: 0 - Disable heuristic analysis. |
|
VirusBlokAda |
No configuration |
|
|
Zillya |
[engine] |
load_extended_daabase: engine will load a larger database 0 - faster initialization, but lower detection rate |
|
Antiy |
[engine] |
deep_scan : 0 - lower memory usage |
|
McAfee |
[engine] |
|
|
NanoAV |
[engine] |
|
|
NETGATE |
No configuration |
|
|
Sophos |
[engine] |
|
|
Aegislab |
[engine] |
|
|
ByteHero |
[engine] |
|
|
Filseclab |
[engine] |
heuristic_scan: 0 - Disable heuristic analysis. |
|
Lavasoft |
[engine] |
|
|
STOPzilla |
[engine] |
|
|
Symantec |
[engine] |
should not change server value, it's the ip and host where Symantec service is running. |
|
Systweak |
[engine] |
|
|
Huorong |
[engine] |
|
|
Comodo |
[engine] |
|
|
Trend Micro and Trend Micro House Call |
[engine] |
|
|
Xvirus |
No configuration |
|
|
RocketCyber |
No configuration |
|
|
CrowdStrike Falcon ML |
No configuration |
|
|
Windows Defender |
No configuration |
|
|
Microsoft Security Essentials |
No configuration |
|
-
Values in the table are default values
-
If there is no special note, available values are 0 and 1
-
After applying new configuration, need to wait for 30s-60s for engine reloading
-
nProtect was renamed to TACHYON from 6/20/2018
-
Cloud scan feature (enable_cloud_scan) only sends file signatures to AV servers to analyze