9.3.1.2. AMI - Single MetaDefender Deployment
For a single deployment of MetaDefender in a public subnet, refer to the CloudFormation script provided as example.
In this example, besides the MetaDefender EC2 instance, additional resources are being generated and set up.
Deployment flow:
Select the desired MetaDefender, based on the OS support:
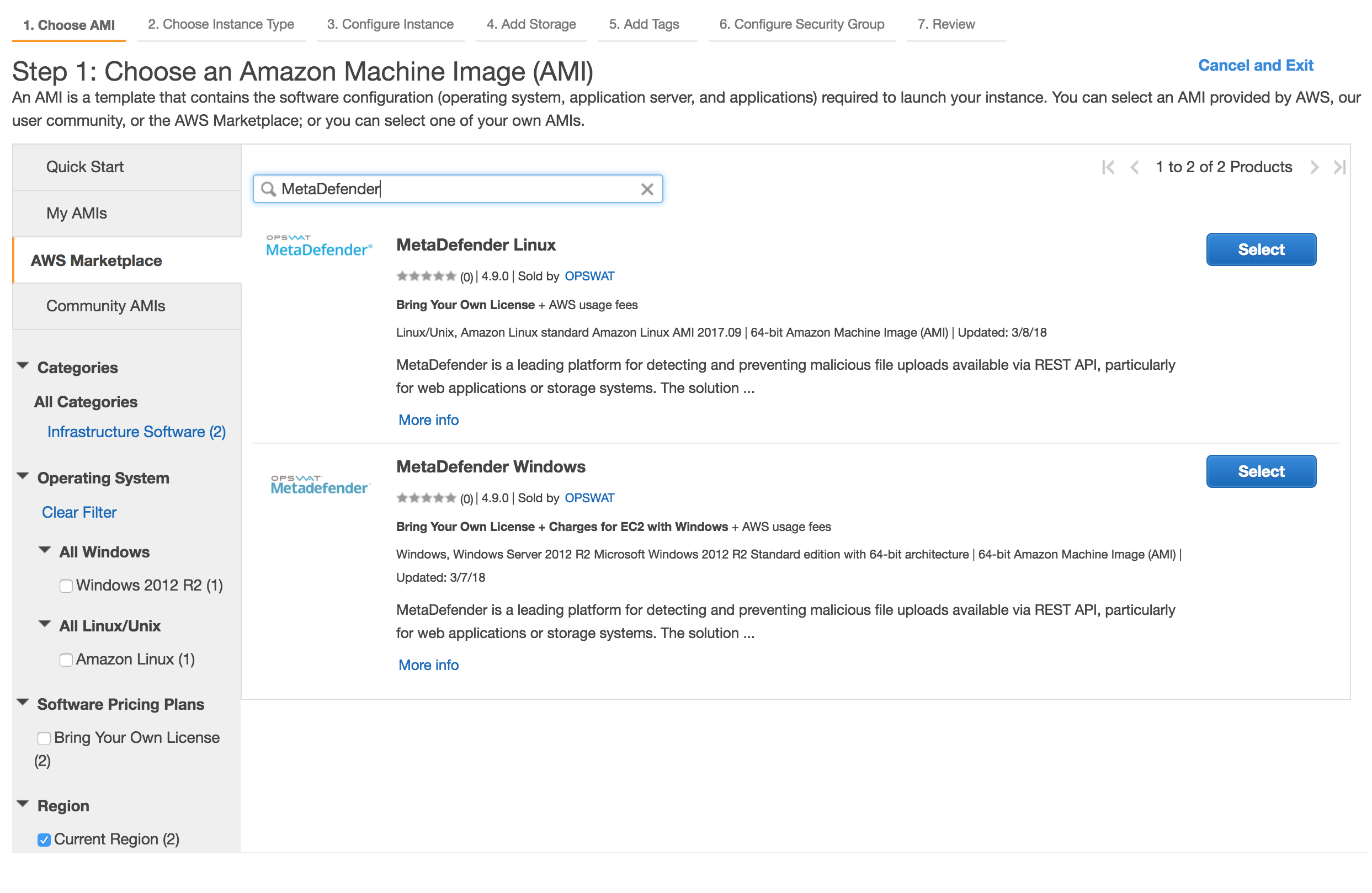
Go through the steps to launch an instance (steps defined here: 9.3.1.1. Install MetaDefender in AWS EC2)
Or, use the CloudFormation template available on OPSWAT's Github account. Feel free to review it and modify it accordingly.
To launch the CloudFormation script, follow these steps:
-
Go to CloudFormation > Create Stack and select the template (or import it):
-
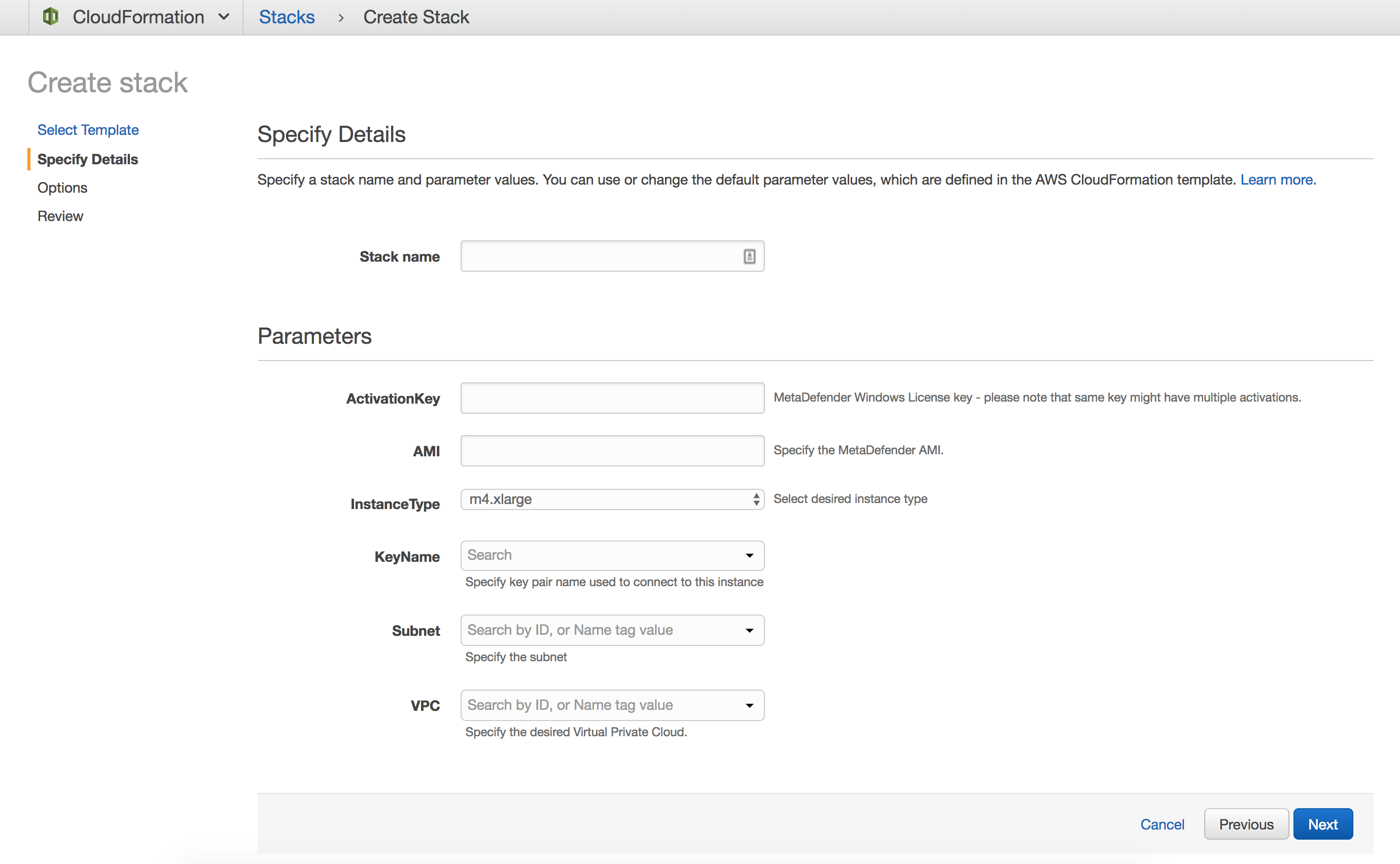
Fill the needed details:
-
Stack name : Identifier for this entire MetaDefender stack
-
Activation Key: MetaDefender license key
-
AMI: grab the AMI id from the AWS Marketplace or from your own built MetaDefender AMI
-
KeyName: the keypair you would like to use in order to manage this instance
-
Note that it's very important to provide a valid key, especially if you plan to connect to this machine for different investigations
-
-
VPC and Subnet: Select from the dropdown which is the VPC and the subnet used for this instance.
-
Note that it's very important that the selected subnet will provide MetaDefender Internet access, in order to get all the needed updates.
-
-
-
-
Finish the wizard, acknowledge that IAM roles are being generated and hit Create
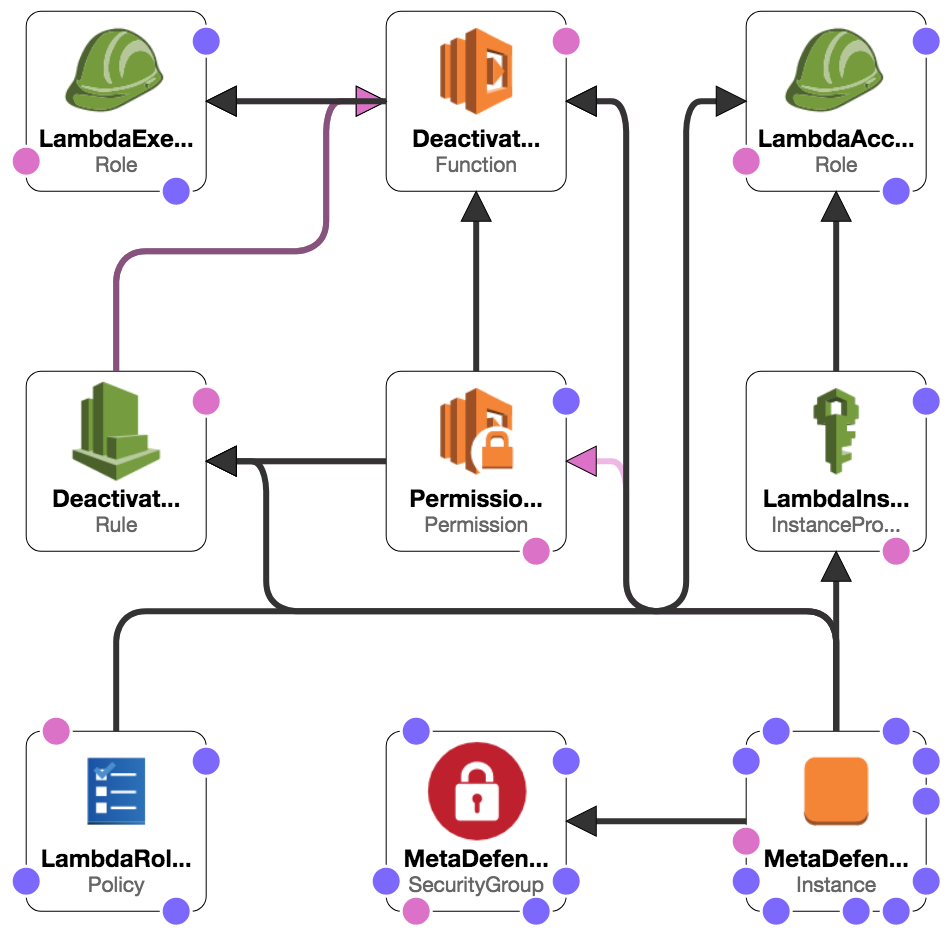
The CloudFormation script will generate the needed resources to provide the following flow:
-
Instance initialize phase
-
User Data script (Powershell for Windows and shell for Linux) will be called which will:
-
change the credentials from the default admin/admin to admin/instance-id
-
updates the CloudWatch Event Rule to be dispatched only for the instances running MetaDefender (adds the new instance-id to the existing list)
-
updates the Deactivate Lambda function by mapping the instance-id to the MetaDefender's unique deploymentId
-
activate the product based on the provided activation key
-
-
-
Instance shutting-down / terminate
-
Deactivate Lambda function will call the OPSWAT Activation Server to deregister the existing MetaDefender deployment
-
Results are logged in CloudWatch
-
-
-
Instance rebooted
-
Respects same flow as Initialize phase
-
Resources:
-
MetaDefender Windows EC2
-
The VM running the MetaDefender instance
-
-
MetaDefenderSecurityGroup
-
Only the TCP port 8008 is opened, being the only port needed to communicate with MetaDefender
-
-
LambdaAccessRole
-
IAM Role created for to the EC2 instance, to allow it to update the DeactivateLambda function and the DeactivateEventRule
-
-
LambdaRolePolicies
-
The IAM Policy which grants access to update the defined lambda function and CloudWatch event rule
-
-
LambdaInstanceProfile
-
IAM InstanceProfile that is attached to the EC2 instance
-
-
DeactivateLambda
-
Calls the OPSWAT's Activation Server to deregister the MetaDefender instance on termination.
-
-
LambdaExecutionRole
-
IAM Role to allow running the lambda function and publishing the results in logs
-
-
DeactivateEventRule
-
CloudWatch EventRule which allows to monitor the EC2 instance and calls DeactivateLambda on shutting-down or stopping.
-
-
PermissionForEventsToInvokeLambda
-
Lambda Permission needed to invoke the DeactivateLambda function
-
-
Resources and relationships:
-